Crooks use HTML smuggling to spread QBot malware via SVG files
Security Affairs
DECEMBER 14, 2022
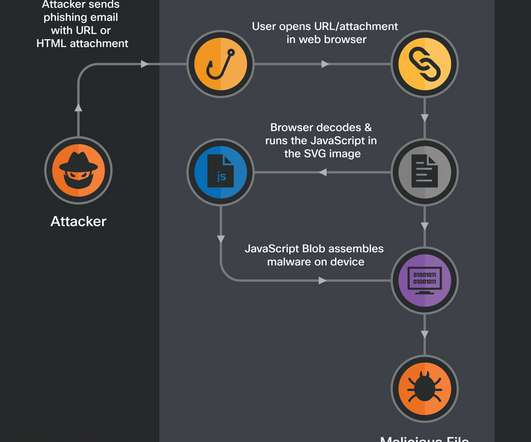
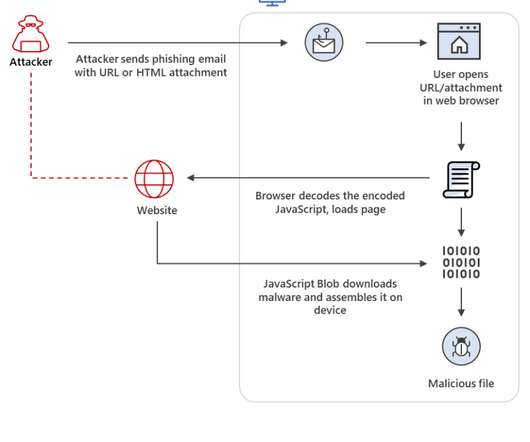
The malicious HTML code is generated within the browser on the target device which is already inside the security perimeter of the victim’s network. . “SVG images are constructed using XML, allowing them to be placed within HTML using ordinary XML markup tags. ” reads the analysis published by Talos.


















Let's personalize your content