Google TAG warns that Russian COLDRIVER APT is using a custom backdoor
Security Affairs
JANUARY 18, 2024
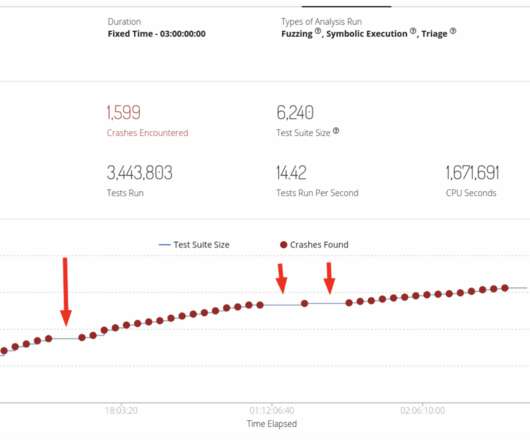
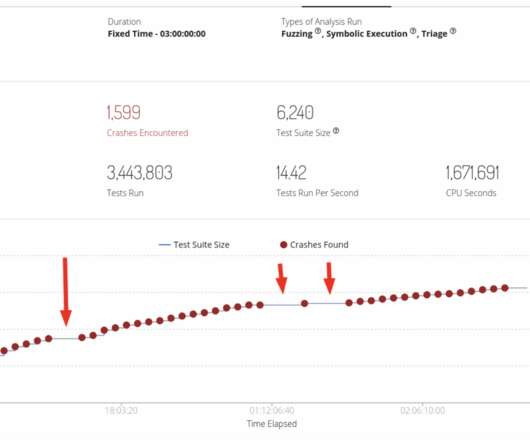
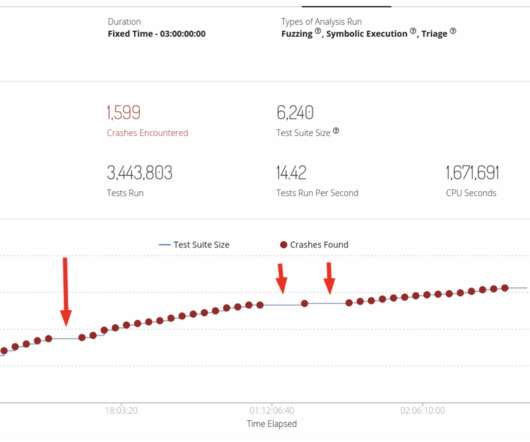
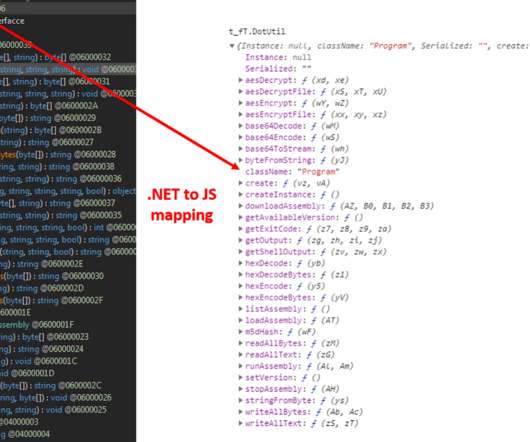
Google TAG researchers warn that COLDRIVER is evolving tactics, techniques and procedures (TTPs), to improve its detection evasion capabilities. Recently, TAG has observed COLDRIVER delivering custom malware via phishing campaigns using PDFs as lure documents. ” reads TAG’s analysis. ” concludes the report.































Let's personalize your content