Productivity Tools May Be Monitoring Workers' Productivity
Data Breach Today
NOVEMBER 27, 2020
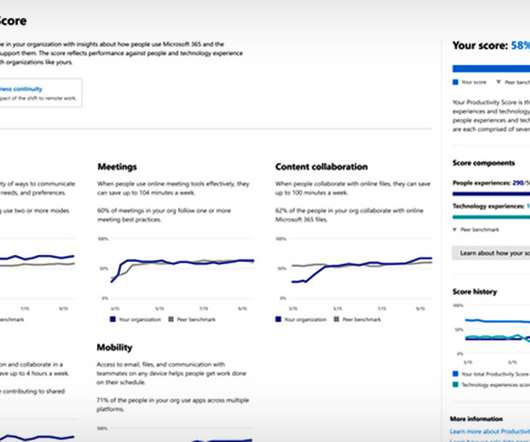
Regulatory and Employee Litigation Risks Face Businesses That Violate Privacy Rules Warning to workers: Your productivity tools may also be tracking your workplace productivity, and your bosses may not even know it.


















































Let's personalize your content