Who’s Behind the ‘Web Listings’ Mail Scam?
Krebs on Security
MARCH 23, 2020
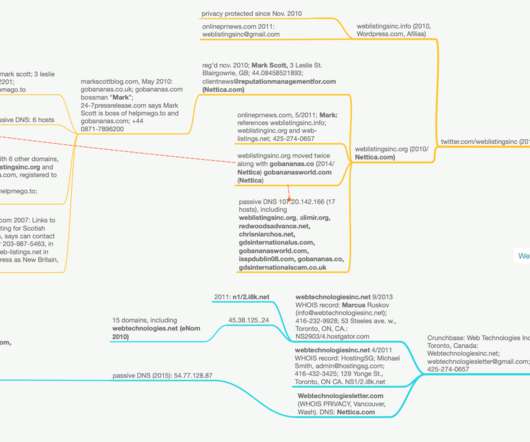
In December 2018, KrebsOnSecurity looked at how dozens of U.S. Information about who registered Webtechnologiesletter.com is completely hidden behind privacy protection services. web-listings.net 2007-04-24 ENOM, INC.,ENOM, weblistingservices.com 2007-04-23 ENOM, INC.,ENOM, web-listings.net 2007-04-24 ENOM, INC.,ENOM,















Let's personalize your content