ZLoader Malware adds Zeus’s anti-analysis feature
Security Affairs
MAY 3, 2024
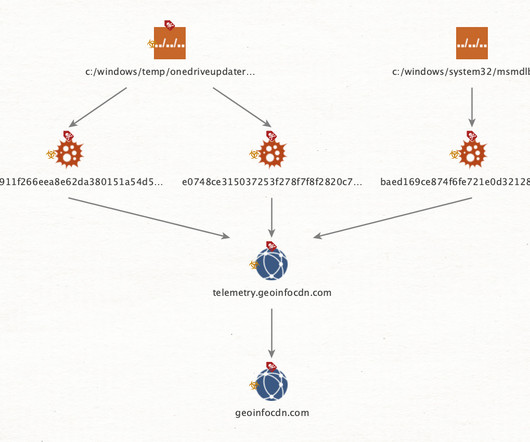
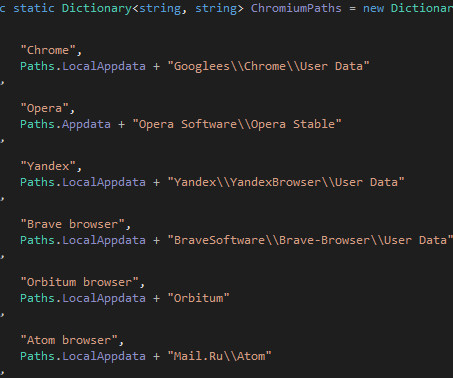
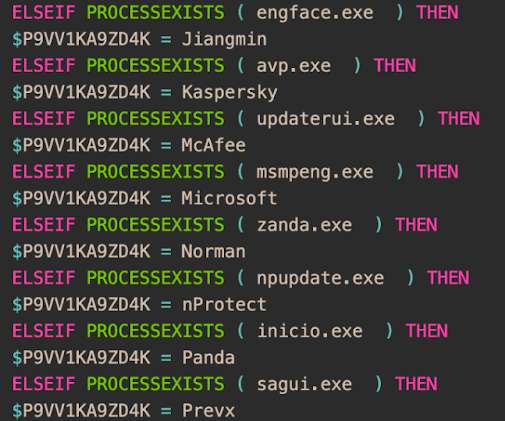
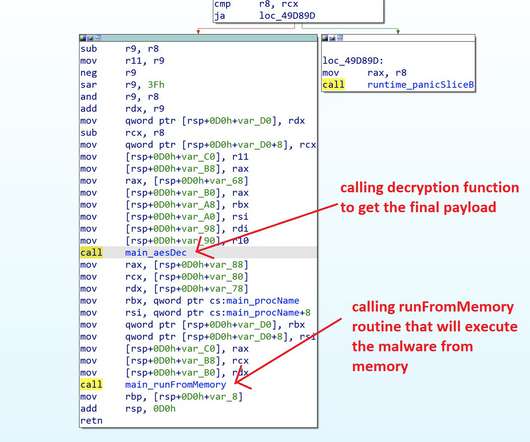
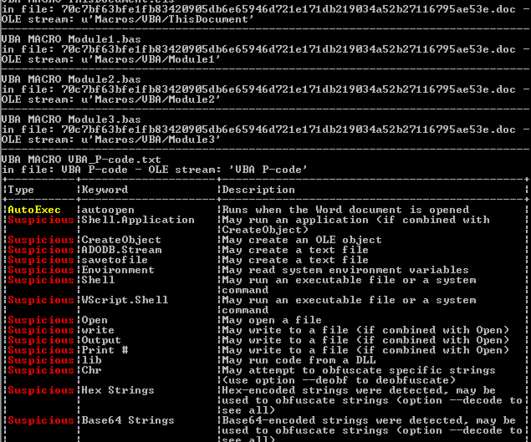
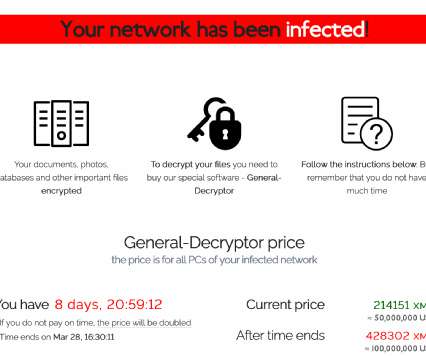
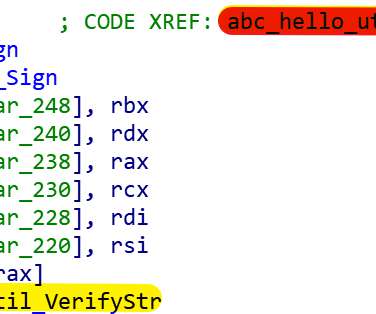
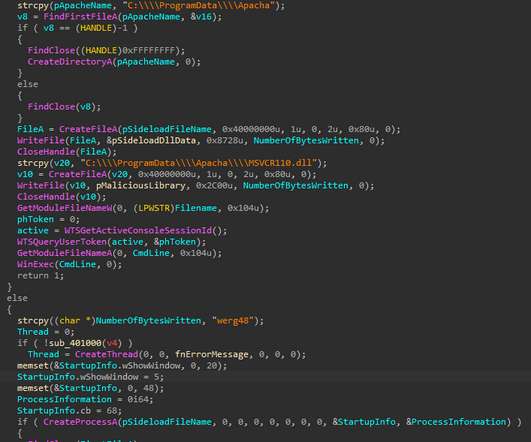
Zloader (aka Terdot, DELoader, or Silent Night) is a modular trojan based on the leaked ZeuS source code. This feature prevents malware execution outside the infected machine, a feature that had been abandoned by many malware variants that borrow the Zeus leaked source code. X source code, but implemented differently.”

















Let's personalize your content