Targeted operation against Ukraine exploited 7-year-old MS Office bug
Security Affairs
APRIL 28, 2024
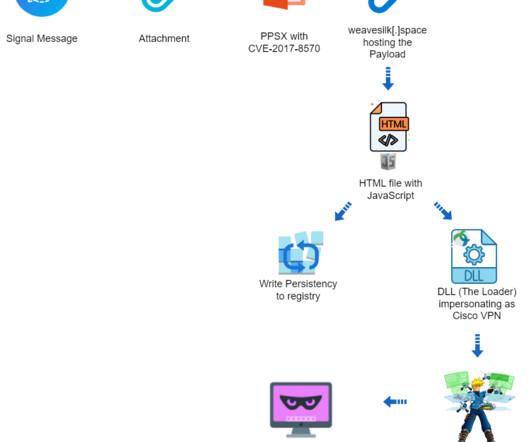
Security experts at Deep Instinct Threat Lab have uncovered a targeted campaign against Ukraine, exploiting a Microsoft Office vulnerability dating back almost seven years to deploy Cobalt Strike on compromised systems. The DLL also implements features to evade detection and avoid analysis by security experts. space and petapixel[.]fun

























Let's personalize your content