Top Initial Attack Vectors: Passwords, Bugs, Trickery
Data Breach Today
SEPTEMBER 14, 2021
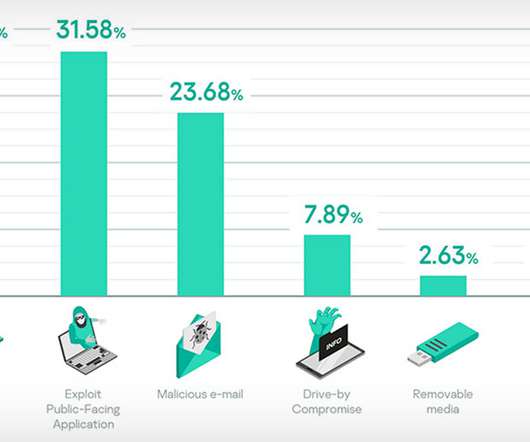
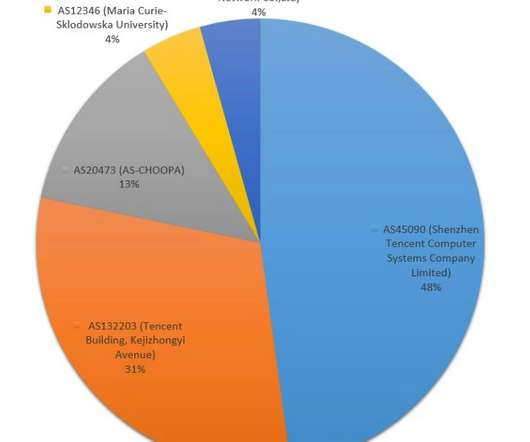
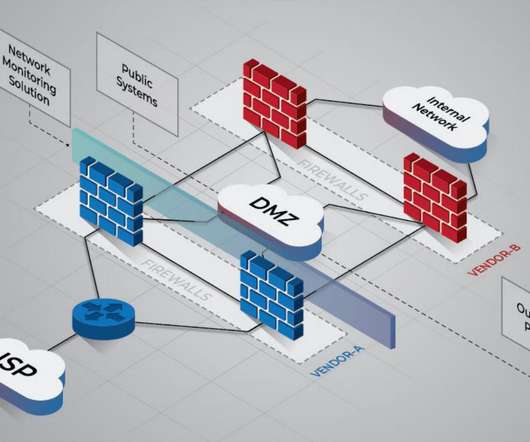
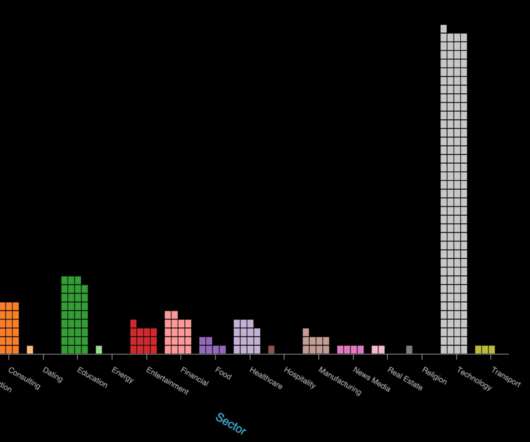
Use of LOLBins, GitHub Tools and Cobalt Strike Also Widespread, Researchers Say The top three tactics attackers have been using to break into corporate and government networks are brute-forcing passwords, exploiting unpatched vulnerabilities, and social engineering via malicious emails, says security firm Kaspersky in a roundup of its 2020 incident (..)










































Let's personalize your content