New DNS Spoofing Threat Puts Millions of Devices at Risk
eSecurity Planet
MAY 3, 2022
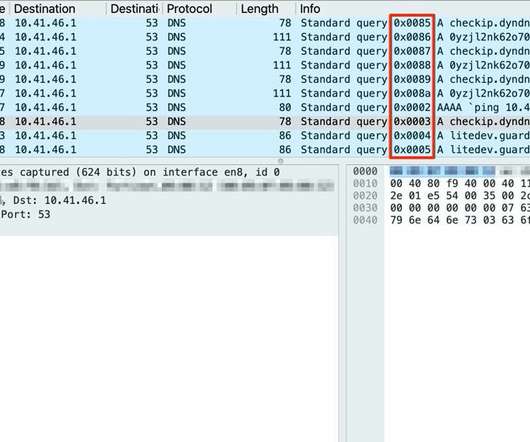
Security researchers have uncovered a critical vulnerability that could lead to DNS spoofing attacks in two popular C standard libraries that provide functions for common DNS operations. The C Library DNS Vulnerability. Nozomi Labs found a pattern in the DNS lookups made with the C libraries (see screenshot below).

































Let's personalize your content