PoC exploit for critical RCE flaw in Fortra FileCatalyst transfer tool released
Security Affairs
MARCH 18, 2024
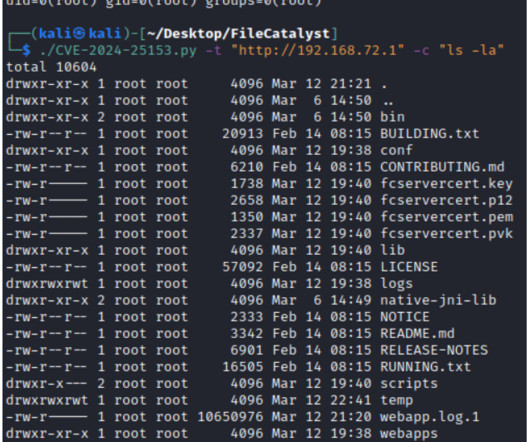
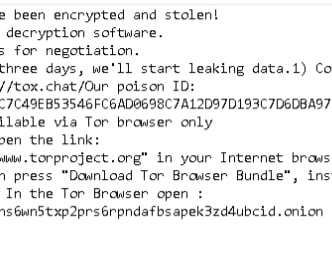
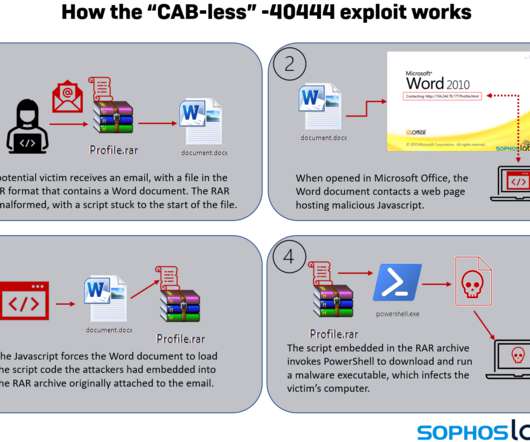
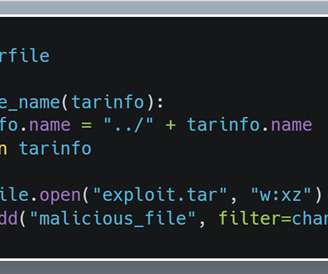
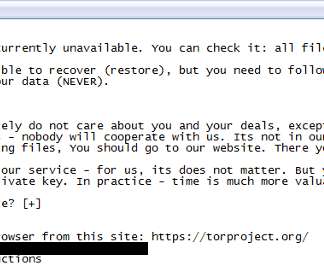
The PoC exploit demonstrates how to upload a web shell on vulnerable instances to execute operating system commands. Upload a command shell with a pseudo-randomly generated file name. Researchers from Nettitude released on GitHub a full proof-of-concept exploit for this vulnerability. Get a valid session token.





































Let's personalize your content