Lilith: The Latest Threat in Ransomware
eSecurity Planet
JULY 19, 2022
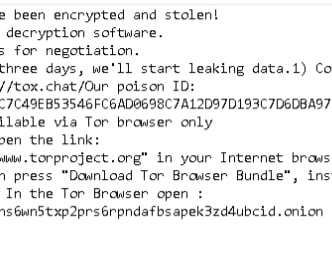
According to Cyble, “The ransomware searches for files to encrypt on the local system by enumerating the file directories […] It ignores the file extensions such as EXE, DLL, and SYS and excludes a list of directory and file names from the encryption process.”. How to Protect Against Lilith Ransomware.






















Let's personalize your content