New HiatusRAT campaign targets Taiwan and U.S. military procurement system
Security Affairs
AUGUST 21, 2023
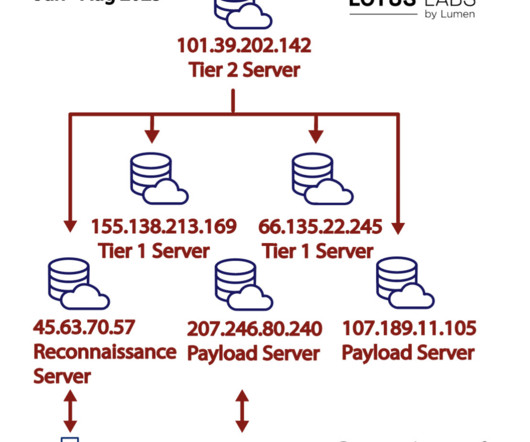
military procurement system. In June the group started a reconnaissance and targeting activity aimed at a U.S. military server used for contract proposals and submissions. We suspect the HiatusRAT cluster serves as another example of tradecraft that could be applied against the U.S. ” continues the report.




























Let's personalize your content