MY TAKE: PKI, digital certificates now ready to take on the task of securing digital transformation
The Last Watchdog
FEBRUARY 21, 2020
Related: Why PKI is well-suited to secure the Internet of Things PKI is the authentication and encryption framework on which the Internet is built. I had a chance to interview Brian Trzupek , DigiCert’s senior vice president of emerging markets products, at the company’s Security Summit 2020 in San Diego recently.



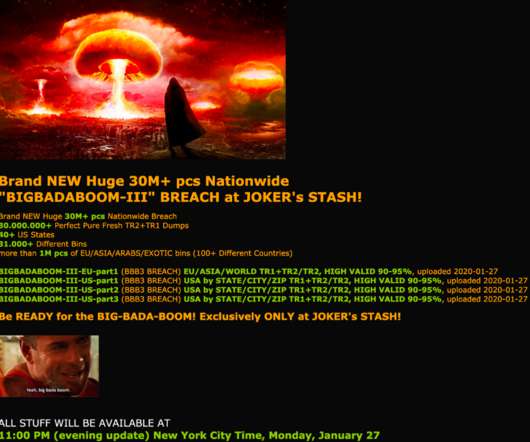



















Let's personalize your content