6 Eye-Opening Statistics About Software Supply Chain Security
Dark Reading
OCTOBER 27, 2021
The latest facts and figures on the state of software supply chain security in the enterprise.

Dark Reading
OCTOBER 27, 2021
The latest facts and figures on the state of software supply chain security in the enterprise.

eSecurity Planet
OCTOBER 26, 2021
As threat actors aim at IT supply chains , enhanced cybersecurity has been the recent driving force for industry adoption of the Software Bill of Materials (SBOM) framework. With a simple list of components that make up a software product, SBOMs enhance transparency between software buyers and sellers, provide the necessary visibility to identify vulnerabilities , and enable rapid incident response.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
OCTOBER 27, 2021
Why do so many HIPAA -covered entities and their vendors do such a poor job managing security risk and safeguarding patient's protected health information? Many critical factors come into play, say Roger Severino, ex- director of HHS OCR, and Bob Chaput, founder of security consultancy Clearwater.
Krebs on Security
OCTOBER 25, 2021
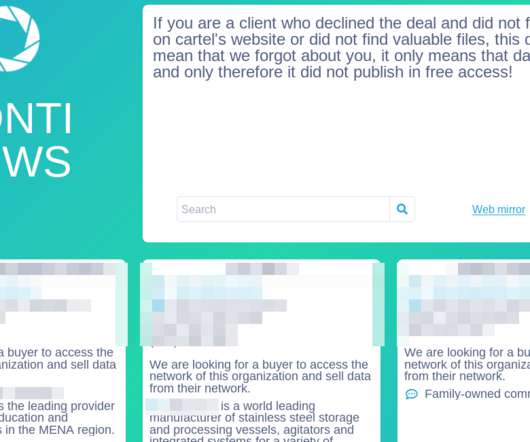
The Conti ransomware affiliate program appears to have altered its business plan recently. Organizations infected with Conti’s malware who refuse to negotiate a ransom payment are added to Conti’s victim shaming blog, where confidential files stolen from victims may be published or sold. But sometime over the past 48 hours, the cybercriminal syndicate updated its victim shaming blog to indicate that it is now selling access to many of the organizations it has hacked.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

The Last Watchdog
OCTOBER 26, 2021
Our Public Key Infrastructure is booming but also under a strain that manual certificate management workflows are not keeping up with. Related: A primer on advanced digital signatures. PKI and digital certificates were pivotal in the formation of the commercial Internet, maturing in parallel with ecommerce. With digital transformation leading to a boom in the use of digital certificates, our bedrock authentication and encryption framework is at an inflection point, where the demand and adoption
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Data Breach Today
OCTOBER 25, 2021
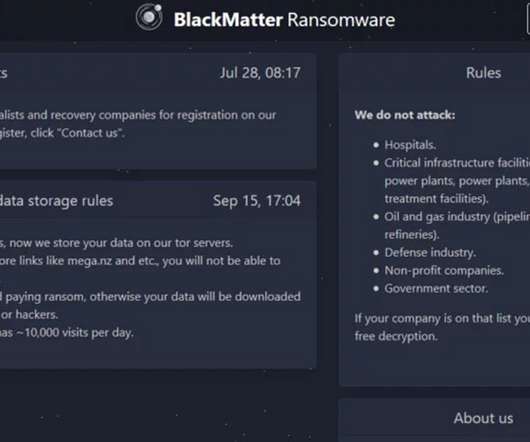
Flaw in DarkSide and BlackMatter Enabled Security Firm to Decrypt Files for Free While ransomware might be today's top cybercrime boogeyman, attackers aren't infallible. The latest example: Errors in DarkSide - and its BlackMatter rebrand - enabled security experts to quietly decrypt many victims' files for free, saving millions in potential ransom payments.
Krebs on Security
OCTOBER 28, 2021
In December 2018, bling vendor Signet Jewelers fixed a weakness in their Kay Jewelers and Jared websites that exposed the order information for all of their online customers. This week, Signet subsidiary Zales.com updated its website to remediate a nearly identical customer data exposure. Last week, KrebsOnSecurity heard from a reader who was browsing Zales.com and suddenly found they were looking at someone else’s order information on the website, including their name, billing address, sh

The Last Watchdog
OCTOBER 25, 2021
When it comes to cyber attacks, most businesses think: “It could never happen to us,” but some plots are just hitting a little too close to home. Related: T-Mobile breach reflects rising mobile device attacks. For instance, if you’ve ever played Grand Theft Auto, you know the goal is quite simply mass destruction: Use whatever resources you have at your disposal to cause as much damage as you possibly can and just keep going.
Security Affairs
OCTOBER 23, 2021
The U.S. CISA warned of crypto-mining malware hidden in a popular JavaScript NPM library, named UAParser.js, which has millions of weekly downloads. The U.S. Cybersecurity and Infrastructure Security Agency published an advisory to warn of the discovery of a crypto-mining malware in the popular NPM Package UAParser.js. The popular library has million of weekly downloads. “Versions of a popular NPM package named ua-parser-js was found to contain malicious code.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Data Breach Today
OCTOBER 25, 2021
Move by Colonial Pipeline Attackers Follows Law Enforcement Action Against REvil Following an outage of the REvil - aka Sodinokibi - ransomware operation due to coordinated law enforcement efforts involving the U.S. and foreign partners, the operators behind DarkSide ransomware have moved Bitcoin worth almost $7 million to multiple new wallets, making it more difficult to track.

DXC Technology
OCTOBER 27, 2021
Are you trying to introduce new ways of working and deliver new value to your business via cloud while having to cope with legacy technologies (which will potentially be around for years to come)? Are you trying to fit your old ways of working onto your new technologies? These are situations that we typically see, […]. The post Hybrid IT: Cloud and legacy tech must live together in peace appeared first on DXC Blogs.

The Last Watchdog
OCTOBER 28, 2021
Over the past five years, cryptocurrency exchanges have been the target of increasingly damaging “ 51% attacks ” resulting in the theft of over $30 million worth of cryptocurrency to date. Related: Wildland restores control of data to individuals. However, these attacks aren’t due to exchange security flaws; malicious actors are exploiting the underlying consensus protocols of blockchains themselves.

Security Affairs
OCTOBER 23, 2021
Cisco fixes an OS command-injection flaw, tracked as CVE-2021-1529, in Cisco SD-WAN that could allow privilege escalation and lead to arbitrary code execution. Cisco addressed a high-severity OS command-injection vulnerability, tracked as CVE-2021-1529, in Cisco SD-WAN that could allow privilege escalation and lead to arbitrary code execution. Cisco SD-WAN is a cloud-delivered overlay WAN architecture that enables digital and cloud transformation at enterprises, it allows to connect disparate of

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.
Data Breach Today
OCTOBER 27, 2021
Rebranding Remains Easy for Ransomware Groups, While Affiliates Already Come and Go Will the notorious ransomware operation known as REvil, aka Sodinokibi, reboot yet again after someone apparently messed with its infrastructure? Experts suggest that the operation's brand is burned, and administrators will launch a new group. Many affiliates, meanwhile, already work with multiple groups.

Threatpost
OCTOBER 29, 2021
Malware delivered via a compromised website on Chrome browsers can bypass User Account Controls to infect systems and steal sensitive data, such as credentials and cryptocurrency.
IT Governance
OCTOBER 26, 2021
Welcome to our third quarterly review of security incidents for 2021, in which we take a closer look at the information gathered in our monthly list of cyber attacks and data breaches. In this article, you’ll find an overview of the cyber security landscape from the past three months, including the latest statistics and our observations. This includes year-on-year comparisons in the number of publicly disclosed incidents, a review of the most breached sectors and a running total of incidents for

Security Affairs
OCTOBER 26, 2021
The FBI published a flash alert to warn of the activity of the Ranzy Locker ransomware that had already compromised tens of US companies. The FBI published a flash alert to warn of Ranzy Locker ransomware operations that had already compromised at least 30 US companies this year. The gang has been active since at least 2020, threat actors hit organizations from various industries. “Unknown cyber criminals using Ranzy Locker ransomware had compromised more than 30 US businesses as of July 2

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Data Breach Today
OCTOBER 28, 2021
Incident Is Among Latest Involving Healthcare Supply Chain Vendors A ransomware attack on a medical practice management services firm that included the theft of files containing patient information is among the latest security incidents involving similar third-party vendors.

DLA Piper Privacy Matters
OCTOBER 27, 2021
The case of Dr Mary Fairhurst -v- Mr Jon Woodard illustrates the risks associated with the installation of security cameras and why it is vital to ensure a lawful basis for capturing and processing such images exists. Our article on this recent English court case is available by clicking here.

Schneier on Security
OCTOBER 28, 2021
Microsoft is reporting that the same attacker that was behind the SolarWinds breach — the Russian SVR, which Microsoft is calling Nobelium — is continuing with similar supply-chain attacks: Nobelium has been attempting to replicate the approach it has used in past attacks by targeting organizations integral to the global IT supply chain.

Security Affairs
OCTOBER 28, 2021
German authorities have identified a Russian man named Nikolay K. who is suspected to be a prominent member of the REvil ransomware gang. REvil ransomware gang is one of the most successful ransomware operations, the group and its affiliated hit hundreds of organizations worldwide. On July 2, the gang hit the Kaseya cloud-based MSP platform impacting MSPs and their customers, it asked $70 million worth of Bitcoin for decrypting all impacted systems.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Data Breach Today
OCTOBER 29, 2021
VMware’s Tom Kellermann on Defending Against Ransomware Attacks In ransomware attacks, cybercriminals attack through the backups because they know that security practitioners rely on backups to save themselves after a ransomware attack. Therefore, it is essential to have multiple backups, says Tom Kellermann, head of cybersecurity strategy at VMware.

Dark Reading
OCTOBER 27, 2021
Most IT and security leaders are confident their cybersecurity strategy is on the right track, but they still believe their organizations are as vulnerable as they were a year ago.

Schneier on Security
OCTOBER 27, 2021
Vice has a detailed article about how the FBI gets data from cell phone providers like AT&T, T-Mobile, and Verizon, based on a leaked (I think) 2019 139-page presentation.
Security Affairs
OCTOBER 27, 2021
Grief ransomware operators claim to have compromised computer systems at US National Rifle Association (NRA) and added it to their leak site. Grief ransomware operators announced to have hacked US National Rifle Association (NRA) and threaten to leak the stolen data. The NRA was added to the list of compromised organizations on the leak site of the group, that gang also published a set of documents as proof of the hack.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Data Breach Today
OCTOBER 25, 2021
The Rant of the Day From Ian Keller, Ericsson In his second Rant of the Day for the CyberEdBoard Profiles in Leadershop blog, Ian Keller, security director at Ericsson and CyberEdBoard executive member, talks about what a CISO does - and what a CISO should do.

Data Matters
OCTOBER 26, 2021
On 7 October 2021, the Information Commissioner’s Office (“ ICO ”), published its response to the UK government’s consultation entitled “Data: A new direction”. The consultation which sets out the proposals of the Department for Digital, Culture Media & Sport (“ DCMS ”) promised far-reaching reforms to the UK data protection regime with an emphasis on capturing the power of data to drive economic growth and innovation.

Hunton Privacy
OCTOBER 25, 2021
As reported on the Hunton Retail Resource Blog , on October 20, 2021, a new wave in the fight against “robocalls” is targeting telemarketing text messages. In the past six months, there has been an uptick in activity at both the state and federal level to reign in telemarketing text messages. On July 1, 2021, Florida’s “mini-TCPA” went into effect. The mini-TCPA amends Florida’s Telemarketing Act in several key ways, most notably in allowing consumers to maintain a private cause of action for vi
Let's personalize your content