Malicious PDFs Flood the Web, Lead to Password-Snarfing
Threatpost
JUNE 15, 2021
SolarMarker makers are using SEO poisoning, stuffing thousands of PDFs with tens of thousands of pages full of SEO keywords & links to redirect to the malware.

Threatpost
JUNE 15, 2021
SolarMarker makers are using SEO poisoning, stuffing thousands of PDFs with tens of thousands of pages full of SEO keywords & links to redirect to the malware.
Security Affairs
JUNE 16, 2021
How AI is Transforming Data Governance? Consumers are becoming more aware of their rights, making data governance more relevant across organizations. Data governance is a set of standards, metrics, and processes that allow organizations to responsibly use consumer data.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
JUNE 16, 2021
TorrentFreak surveyed nineteen VPN providers, asking them questions about their privacy practices: what data they keep, how they respond to court order, what country they are incorporated in, and so on. Most interesting to me is the home countries of these companies. Express VPN is incorporated in the British Virgin Islands. NordVPN is incorporated in Panama.

Data Breach Today
JUNE 16, 2021
U.S Wants 16 Critical Infrastructure Entities Off-Limits to Attack At their Geneva summit meeting Wednesday, U.S. President Joe Biden told Russian President Vladimir Putin that if Russia continued to wage cyberattacks against the U.S., it would face retaliation.

Advertisement
Generative AI is upending the way product developers & end-users alike are interacting with data. Despite the potential of AI, many are left with questions about the future of product development: How will AI impact my business and contribute to its success? What can product managers and developers expect in the future with the widespread adoption of AI?

Krebs on Security
JUNE 16, 2021
Authorities in Ukraine this week charged six people alleged to be part of the CLOP ransomware group , a cybercriminal gang said to have extorted more than half a billion dollars from victims. Some of CLOP’s victims this year alone include Stanford University Medical School , the University of California , and University of Maryland. A still shot from a video showing Ukrainian police seizing a Tesla, one of many high-end vehicles seized in this week’s raids on the Clop gang.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
eSecurity Planet
JUNE 18, 2021
There’s a never ending cycle between the measures cybersecurity providers introduce to prevent or remediate cyber threats and the tactics cyber criminals use to get around these security measures. As soon as a security company develops a way to mitigate the latest threat, attackers develop a new threat to take its place. Artificial intelligence has emerged as a critical tool cybersecurity companies leverage to stay ahead of the curve.

Data Breach Today
JUNE 14, 2021
Service Employees International Union 775 Benefits Group: PII and PHI Deleted A Seattle-based benefits administrator for unionized home healthcare and nursing home workers has reported a hacking incident affecting 140,000 individuals that involved deleting certain data.
Krebs on Security
JUNE 15, 2021
The U.S. Department of Justice (DOJ) last week announced the arrest of a 55-year-old Latvian woman who’s alleged to have worked as a programmer for Trickbot , a malware-as-a-service platform responsible for infecting millions of computers and seeding many of those systems with ransomware. Just how did a self-employed web site designer and mother of two come to work for one of the world’s most rapacious cybercriminal groups and then leave such an obvious trail of clues indicating her
Security Affairs
JUNE 18, 2021
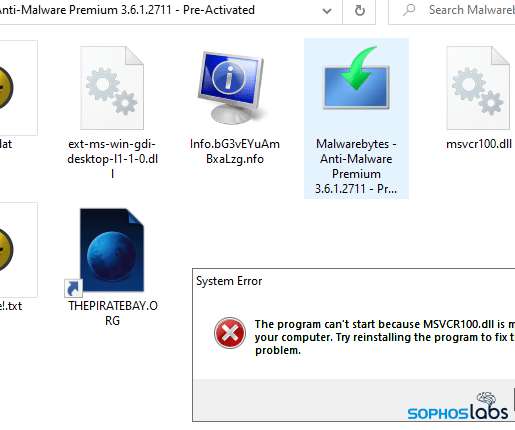
This strange malware stops you from visiting pirate websites. Sophos researchers uncovered a malware campaign that aims at blocking infected users’ from being able to visit a large number of piracy websites. . Sophos researchers uncovered a malware campaign that aims at blocking infected users’ from visiting a large number of websites dedicated to software piracy by modifying the HOSTS file on the infected system.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Troy Hunt
JUNE 14, 2021
Today I'm very happy to welcome the Finnish government to Have I Been Pwned by granting their National Cyber Security Centre full and free access to query their government domains. API access to query their domains will give them greater visibility into the impact of data breaches on the Finnish government. Finland is now the 5th Nordic country and 21st national CERT to be onboarded with many more from around the globe to be announced shortly.

Data Breach Today
JUNE 16, 2021
Database Contains Website Visitor Activity Logs, But Not Personal Information The discovery of an unsecured database containing over 1 billion records related to CVS Health website visitor activity illustrates yet again how security missteps can potentially leave sensitive data exposed, some security experts say.

Krebs on Security
JUNE 18, 2021
In May 2019, KrebsOnSecurity broke the news that the website of mortgage settlement giant First American Financial Corp. [ NYSE:FAF ] was leaking more than 800 million documents — many containing sensitive financial data — related to real estate transactions dating back 16 years. This week, the U.S. Securities and Exchange Commission settled its investigation into the matter after the Fortune 500 company agreed to pay a paltry penalty of less than $500,000.

Security Affairs
JUNE 12, 2021
An authentication bypass flaw in the polkit auth system service used on most Linux distros can allow to get a root shell. An authentication bypass vulnerability in the polkit auth system service, tracked as CVE-2021-3560 , which is used on most Linux distros can allow an unprivileged attacker to get a root shell. “A flaw was found in polkit. When a requesting process disconnects from dbus-daemon just before the call to polkit_system_bus_name_get_creds_sync starts, the process cannot get a

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

The Guardian Data Protection
JUNE 15, 2021
Swedish retailer found guilty of gathering data to sift out potential trouble-makers among employees The home furnishings group Ikea has been ordered to pay €1.1m (£861,000) in fines and damages by a French court after being found guilty of spying on staff. Two former Ikea France executives were also convicted and fined over an elaborate scheme to gather information on hundreds of employees, job applicants and even customers over several years, using private detectives and police sources.

Data Breach Today
JUNE 15, 2021
Data Was Left Unsecured by Unidentified Marketing Services Company Volkswagen and its Audi subsidiary are notifying 3.3 million people in the U.S and Canada of a breach of personal information by a marketing services supplier. Volkswagen says 90,000 of those affected may have also had their driver's license number, loan data and other personal information exposed.

Schneier on Security
JUNE 17, 2021
General Packet Radio Service (GPRS) is a mobile data standard that was widely used in the early 2000s. The first encryption algorithm for that standard was GEA-1, a stream cipher built on three linear-feedback shift registers and a non-linear combining function. Although the algorithm has a 64-bit key, the effective key length is only 40 bits, due to “an exceptional interaction of the deployed LFSRs and the key initialization, which is highly unlikely to occur by chance.” GEA-1 was d

Security Affairs
JUNE 17, 2021
Researchers discovered an unprotected database belonging to CVS Health that was exposed online containing over a billion records. This week WebsitePlanet along with the researcher Jeremiah Fowler discovered an unsecured database, belonging to the US healthcare and pharmaceutical giant CVS Health, that was exposed online. The database was accessible to everyone without any type of authentication. “On March 21st, 2021 the WebsitePlanet research team in cooperation with Security Researcher

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Dark Reading
JUNE 16, 2021
Growing list of similar actions in recent months may finally be scaring some operators into quitting, but threat is far from over, security experts say.

Data Breach Today
JUNE 13, 2021
Joint Effort with US to Maintain a Black List of Hackers Among Plan proposals The U.K. says it plans to turn the country into a global leader in cybersecurity, in partnership with the U.S, to counter threats ranging from ransomware to critical infrastructure attacks, according to a report by U.K. newspaper the Telegraph.

Hunton Privacy
JUNE 16, 2021
After two rounds of public comments, the Data Security Law of the People’s Republic of China (the “DSL”) was formally issued on June 10, 2021, and will become effective on September 1, 2021. Compared to previous drafts of the law, the final version of the DSL differs with respect to: establishing a work coordination mechanism and clarifying the duties of each governmental authority; establishing an administration system for state core data; encouraging data development and use to make public ser

Security Affairs
JUNE 12, 2021
McDonald’s fast-food chain disclosed a data breach, hackers have stolen information belonging to customers and employees from the US, South Korea, and Taiwan. McDonald’s, the world’s largest restaurant chain by revenue, has disclosed a data breach that impacted customers and employees from the US, South Korea, and Taiwan. The hackers compromised the system of the company and have stolen business contact info belonging to US employees and franchises, the company pointed out that

Advertisement
Start-ups & SMBs launching products quickly must bundle dashboards, reports, & self-service analytics into apps. Customers expect rapid value from your product (time-to-value), data security, and access to advanced capabilities. Traditional Business Intelligence (BI) tools can provide valuable data analysis capabilities, but they have a barrier to entry that can stop small and midsize businesses from capitalizing on them.

Dark Reading
JUNE 18, 2021
The more you know, the more you grow. The Edge takes a fresh look at leading security certifications that can help advance your career.

Data Breach Today
JUNE 17, 2021
16 Critical Infrastructure Sectors Especially Off Limits - Or Else, President Warns U.S. President Joe Biden issued a clear warning to Russian President Vladimir Putin at their Geneva summit this week, saying that should Russia continue to launch cyberattacks against U.S. critical infrastructure sectors, or hack software supply chains, then Moscow should expect to see retaliation.
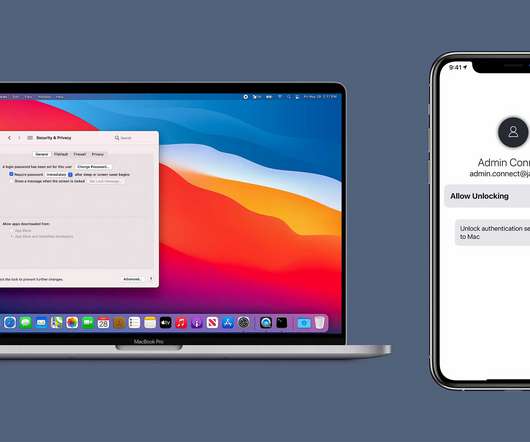
Jamf
JUNE 14, 2021
Jamf Connect expands secure identity and access to resources with Jamf Unlock, passwordless authentication from an iPhone app to securely unlock Mac and the resources needed to be productive.
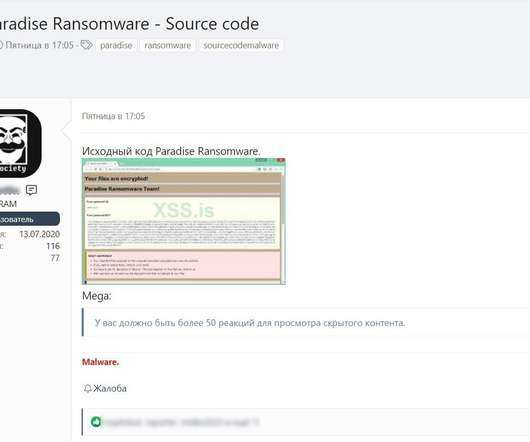
Security Affairs
JUNE 15, 2021
The source code for the Paradise Ransomware has been released on a hacking forum allowing threat actors to develop their customized variant. The source code for the Paradise Ransomware has been released on the hacking forum XSS allowing threat actors to develop their own customized ransomware operation. The news of the availability of the source code was first reported by Tom Malka , a senior threat intelligence analyst for security firm Security, that reported it to BleepingComputer and The Rec

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Hunton Privacy
JUNE 17, 2021
On June 14, 2021, Texas Governor Greg Abbott signed HB 3746 , a bill amending Texas’s data breach notification law. Texas’s breach notification law requires notice to affected residents in the event of a data breach affecting certain sensitive personal data, including Social Security numbers, driver’s license or other government-issued ID numbers, account numbers or payment card numbers in combination with any required security code, access code or password, or certain information about an indiv

Data Breach Today
JUNE 18, 2021
Guidance Spells Out Best Risk Mitigation Practices The U.S. National Security Agency has released new guidance to help federal agencies as well as business enterprises protect their unified communications channels and voice/video over IP calls from cyberthreats.

Threatpost
JUNE 14, 2021
Nearly all of the leaked data was for owners or wannabe owners of the automaker’s luxury brand of Audis, now at greater risk for phishing, ransomware or car theft.
Let's personalize your content