Apple Fixes iOS Kernel Zero-Days Being Exploited in the Wild
Data Breach Today
MARCH 6, 2024
Real-World Scenarios Are Sketchy But Researchers Warn: 'Assume Spyware; Update Now' Apple pushed out an emergency security update for two critical zero-day flaws that attackers are using to carry out memory corruption attacks on iPhone and iPad devices. The tech giant's latest patch addressed its third zero-day vulnerability this year.













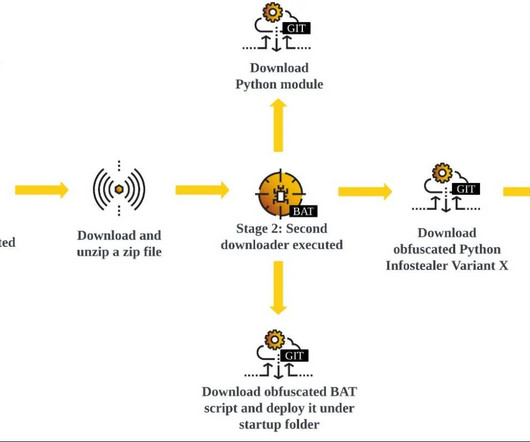



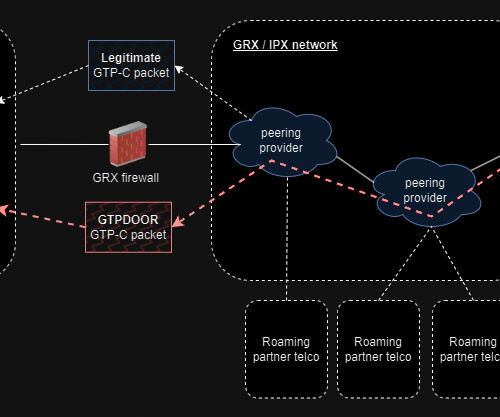









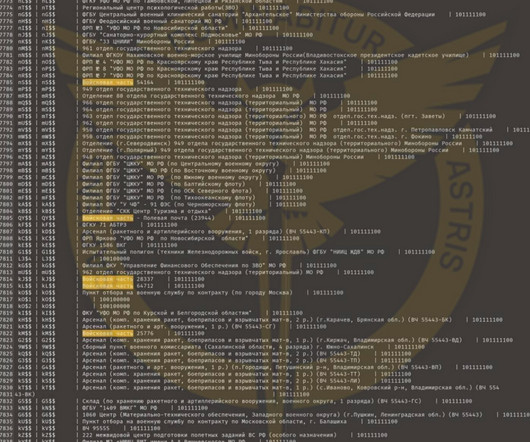













Let's personalize your content