3 Ways ChatGPT Will Change Infosec in 2023
Dark Reading
JANUARY 27, 2023
OpenAI's chatbot has the promise to revolutionize how security practitioners work.

Dark Reading
JANUARY 27, 2023
OpenAI's chatbot has the promise to revolutionize how security practitioners work.

Data Breach Today
JANUARY 6, 2023
Database Will Provide Intelligence of Use to Online Criminals, Expert Warns Expect the recently leaked database containing over 200 million Twitter records to be an ongoing resource for hackers, fraudsters and other criminals operating online, even though 98% of the email addresses it contains have appeared in prior breaches, experts warn.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Krebs on Security
JANUARY 9, 2023
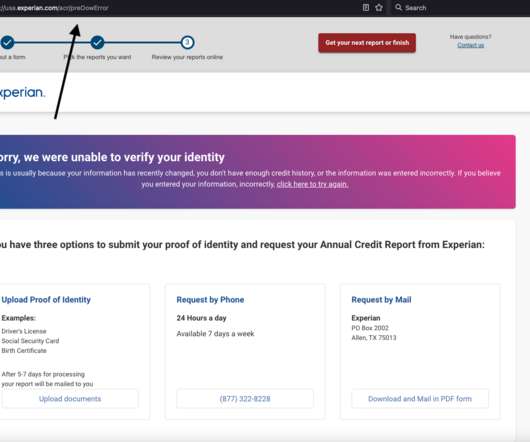
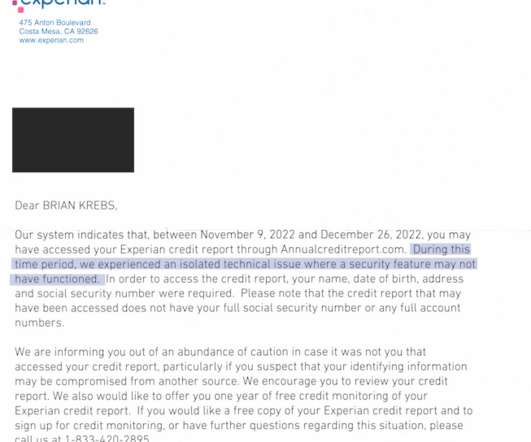
Identity thieves have been exploiting a glaring security weakness in the website of Experian , one of the big three consumer credit reporting bureaus. Normally, Experian requires that those seeking a copy of their credit report successfully answer several multiple choice questions about their financial history. But until the end of 2022, Experian’s website allowed anyone to bypass these questions and go straight to the consumer’s report.

Dark Reading
JANUARY 31, 2023
Everyone on Twitter wants a blue check mark. But Microsoft Azure's blue badges are even more valuable to a threat actor stealing your data via malicious OAuth apps.

Advertisement
With its unparalleled flexibility, rapid development and cost-saving capabilities, open source is proving time and again that it’s the leader in data management. But as the growth in open source adoption increases, so does the complexity of your data infrastructure. In this Analyst Brief developed with IDC, discover how and why the best solution to this complexity is a managed service, including: Streamlined compliance with some of the most complex regulatory guidelines Simplified operations, li

eSecurity Planet
JANUARY 5, 2023
After a year that saw massive ransomware attacks and open cyber warfare, the biggest question in cybersecurity for 2023 will likely be how much of those attack techniques get commoditized and weaponized. “In 2022, governments fought wars online, businesses were affected by multiple ransomware gangs, and regular users’ data was constantly on hackers’ radars,” said NordVPN CTO Marijus Briedis. 2023, he predicted, “will not be any easier when it comes to keeping users’
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
John Battelle's Searchblog
JANUARY 6, 2023
The Very Hardest Thing. What’s the hardest thing you could do as a tech-driven startup? I’ve been asked that question a few times over the years, and my immediate answer is always the same: Trying to beat Google in search. A few have tried – DuckDuckGo has built itself a sizable niche business, and there’s always Bing, thought it’s stuck at less than ten percent of Google’s market (and Microsoft isn’t exactly a startup.

Data Breach Today
JANUARY 12, 2023
Attack Is Disrupting International Mail Export Services The cyber incident at the Royal Mail that is impeding exports from the United Kingdom is reportedly a ransomware attack by the LockBit ransomware-as-a-service group. Britain's national postal service told customers Thursday not to post export items.

Krebs on Security
JANUARY 19, 2023
T-Mobile today disclosed a data breach affecting tens of millions of customer accounts, its second major data exposure in as many years. In a filing with federal regulators, T-Mobile said an investigation determined that someone abused its systems to harvest subscriber data tied to approximately 37 million current customer accounts. Image: customink.com In a filing today with the U.S.

Dark Reading
JANUARY 19, 2023
The credential-stuffing attack, likely fueled by password reuse, yielded personal identifiable information that can be used to verify the authenticity of previously stolen data.

Advertisement
The complexity of financial data, the need for real-time insight, and the demand for user-friendly visualizations can seem daunting when it comes to analytics - but there is an easier way. With Logi Symphony, we aim to turn these challenges into opportunities. Our platform empowers you to seamlessly integrate advanced data analytics, generative AI, data visualization, and pixel-perfect reporting into your applications, transforming raw data into actionable insights.
eSecurity Planet
JANUARY 20, 2023
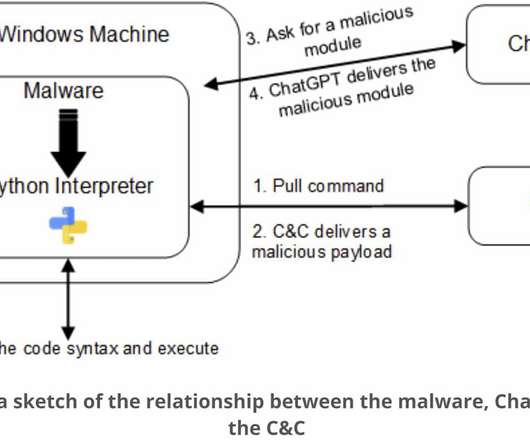
CyberArk researchers are warning that OpenAI’s popular new AI tool ChatGPT can be used to create polymorphic malware. “[ChatGPT]’s impressive features offer fast and intuitive code examples, which are incredibly beneficial for anyone in the software business,” CyberArk researchers Eran Shimony and Omer Tsarfati wrote this week in a blog post that was itself apparently written by AI. “However, we find that its ability to write sophisticated malware that holds no mali

Schneier on Security
JANUARY 17, 2023
No details , though: According to the complaint against him, Al-Azhari allegedly visited a dark web site that hosts “unofficial propaganda and photographs related to ISIS” multiple times on May 14, 2019. In virtue of being a dark web site—that is, one hosted on the Tor anonymity network—it should have been difficult for the site owner’s or a third party to determine the real IP address of any of the site’s visitors.

KnowBe4
JANUARY 20, 2023
An unusual phishing technique has surfaced this week. Avanan, a Check Point Software company, released a blog Thursday morning detailing a new attack in which hackers hide malicious content inside a blank image within an HTML attachment in phishing emails claiming to be from DocuSign.

Data Breach Today
JANUARY 23, 2023
As Funding From Ransoms Goes Down, Gangs Embrace Re-Extortion, Researchers Warn Bad news for ransomware groups: Experts find it's getting tougher to earn a crypto-locking payday at the expense of others. The bad guys can blame a move by law enforcement to better support victims, and more organizations having robust defenses in place, which makes them tougher to take down.

Advertisement
Adding high-quality entity resolution capabilities to enterprise applications, services, data fabrics or data pipelines can be daunting and expensive. Organizations often invest millions of dollars and years of effort to achieve subpar results. This guide will walk you through the requirements and challenges of implementing entity resolution. By the end, you'll understand what to look for, the most common mistakes and pitfalls to avoid, and your options.
Krebs on Security
JANUARY 25, 2023
On Dec. 23, 2022, KrebsOnSecurity alerted big-three consumer credit reporting bureau Experian that identity thieves had worked out how to bypass its security and access any consumer’s full credit report — armed with nothing more than a person’s name, address, date of birth, and Social Security number. Experian fixed the glitch, but remained silent about the incident for a month.

OpenText Information Management
JANUARY 31, 2023
OpenText has completed the acquisition of Micro Focus and I am delighted to welcome customers, partners and employees to OpenText. We are the platform of platforms for Information Management. Digital life is life, and with Micro Focus’ great products, amazing talent and strategic partners, we will help organizations of all sizes accelerate their digital transformations. … The post OpenText Welcomes Micro Focus Customers, Partners and Employees appeared first on OpenText Blogs.

Dark Reading
JANUARY 19, 2023
The "BoldMove" backdoor demonstrates a high level of knowledge of FortiOS, according to Mandiant researchers, who said the attacker appears to be based out of China.
John Battelle's Searchblog
JANUARY 5, 2023
Wise, Kevin Kelly is. Today I’d like to ponder something Kevin Kelly – a fellow co-founding editor of Wired – said to me roughly 30 years ago. During one editorial conversation or another, Kevin said – and I’m paraphrasing here – “The most creative act a human can engage in is forming a good question.” That idea has stuck with me ever since, and informed a lot of my career.

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, VP of Engineering at Betterworks, will explore a practical framework to transform Generative AI pr
IT Governance
JANUARY 9, 2023
Welcome to our review of security incidents for 2022, in which we take a closer look at the information gathered in our monthly lists of data breaches and cyber attacks. Here, you’ll find an overview of the cyber security landscape in 2022, including the total number of publicly disclosed security incidents, the number of compromised records and the sectors most susceptible to data breaches.

Data Breach Today
JANUARY 13, 2023
Bug Exploited Symbolic Links to Find a File Path to Sensitive Data A high-severity vulnerability patched by Google Chrome a few months ago allowed hackers to steal sensitive files such as crypto wallets. Hackers increasingly are targeting individuals and organizations that hold cryptocurrencies, writes Imperva security researcher Ron Masas, who discovered the flaw.
Krebs on Security
JANUARY 10, 2023
Microsoft today released updates to fix nearly 100 security flaws in its Windows operating systems and other software. Highlights from the first Patch Tuesday of 2023 include a zero-day vulnerability in Windows, printer software flaws reported by the U.S. National Security Agency , and a critical Microsoft SharePoint Server bug that allows a remote, unauthenticated attacker to make an anonymous connection.

Schneier on Security
JANUARY 27, 2023
Early in his career, Kevin Mitnick successfully hacked California law. He told me the story when he heard about my new book , which he partially recounts his 2012 book, Ghost in the Wires. The setup is that he just discovered that there’s warrant for his arrest by the California Youth Authority, and he’s trying to figure out if there’s any way out of it.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.
eSecurity Planet
JANUARY 24, 2023
Microsoft’s Visual Studio Code integrated development environment (IDE) is used by as much as 75% of developers, so any security issue has widespread implications. And Aqua Nautilus researchers have discovered a big one. The researchers reported earlier this month that the VSCode editor could be vulnerable to attacks targeting its extensions. The free open source and cross-platform IDE is very easy to use, and there are literally thousands of free extensions developers can install in one c

Dark Reading
JANUARY 5, 2023
A data dump of Twitter user details on an underground forum appears to stem from an API endpoint compromise and large-scale data scraping.

KnowBe4
JANUARY 30, 2023
The UK’s National Cyber Security Centre (NCSC) has described two separate spear phishing campaigns launched by Russia’s SEABORGIUM threat actor and Iran’s TA453 (also known as Charming Kitten). The NCSC says both threat actors have targeted entities in the UK, including “academia, defence, governmental organisations, NGOs, think-tanks, as well as politicians, journalists, and activists.

Data Breach Today
JANUARY 16, 2023
And They’ll Continue to Do So Until Authorities Better Disrupt Them - But How? Pity the overworked ransomware gang - say, LockBit - that just "discovered" one of its affiliates hit Britain's postal service. But until Western governments find a way to truly disrupt the ransomware business model, operators remain free to keep spouting half-truths and lies at victims' expense.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.

Hunton Privacy
JANUARY 3, 2023
On December 21, 2022, the Colorado Attorney General published an updated version of the draft rules to the Colorado Privacy Act (“CPA”). The draft, which follows the first iteration of the proposed rules published on October 10, 2022, solicits comments on five topics: (1) new and revised definitions; (2) the use of IP addresses to verify consumer requests; (3) a proposed universal opt-out mechanism; (4) streamlining the privacy policy requirements; and (5) bona fide loyalty programs.

Schneier on Security
JANUARY 20, 2023
From an article about Zheng Xiaoqing, an American convicted of spying for China: According to a Department of Justice (DOJ) indictment, the US citizen hid confidential files stolen from his employers in the binary code of a digital photograph of a sunset, which Mr Zheng then mailed to himself.

eSecurity Planet
JANUARY 11, 2023
Microsoft’s first Patch Tuesday of 2023 addresses 98 vulnerabilities, more than twice as many as last month – including one zero-day flaw that’s being actively exploited, as well as 11 critical flaws. The zero-day, CVE-2023-21674 , is a Windows Advanced Local Procedure Call (ALPC) elevation of privilege vulnerability with a CVSS score of 8.8.
Let's personalize your content