Building America's Cybersecurity Infrastructure
Dark Reading
JUNE 2, 2022
The government is putting the right skills and expertise in place to fight the rising cyber threat.

Dark Reading
JUNE 2, 2022
The government is putting the right skills and expertise in place to fight the rising cyber threat.

Data Breach Today
JUNE 2, 2022
FBI Director Says Boston Children's Hospital Was Targeted Last Summer Boston Children's Hospital thwarted a cyberattack by government-backed Iranian hackers last summer after U.S. authorities received intelligence about the pending assault and alerted the hospital, says FBI Director Christopher Wray, who called Iran's planned cyberattack "despicable.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
JUNE 2, 2022
Third-Party Risk Management ( TPRM ) has been around since the mid-1990s – and has become something of an auditing nightmare. Related: A call to share risk assessments. Big banks and insurance companies instilled the practice of requesting their third-party vendors to fill out increasingly bloated questionnaires, called bespoke assessments, which they then used as their sole basis for assessing third-party risk.

Data Breach Today
JUNE 2, 2022
Boosting Ukraine's Cyber Space Is Not a Violation of Policy, White House Says The U.S. has conducted offensive cyber activities in support of Ukraine, Cyber Command Director Gen. Paul Nakasone reportedly said on Wednesday at the NATO Cooperative Cyber Defense Center of Excellence conference. The White House says these operations do not violate historic policies with Moscow.

Advertisement
It’s no surprise that Apache Cassandra has emerged as a popular choice for organizations of all sizes seeking a powerful solution to manage their data at a scale—but with great power comes great responsibility. Due to the inherent complexity of distributed databases, this white paper will uncover the 10 rules you’ll want to know when managing Apache Cassandra.

The Last Watchdog
JUNE 2, 2022
Companies have come to depend on Software as a Service – SaaS — like never before. Related: Managed security services catch on. From Office 365 to Zoom to Salesforce.com, cloud-hosted software applications have come to make up the nerve center of daily business activity. Companies now reach for SaaS apps for clerical chores, conferencing, customer relationship management, human resources, salesforce automation, supply chain management, web content creation and much more, even security.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

eSecurity Planet
JUNE 2, 2022
More than 3.6 million MySQL servers are publicly exposed on the internet, security researchers noted this week. Shadow Server Foundation researchers reported that they simply issued a MySQL connection request on default port 3306 to see if a server responded with a MySQL Server Greeting, rather than intrusive requests that pentesters use to break into databases.

Data Breach Today
JUNE 2, 2022
Chris Novak of Verizon Business Group on Latest Breach Investigations Report The 15th edition of the annual Verizon Data Breach Investigations Report examines the rapid growth in ransomware, along with other threat vectors. Chris Novak, global director of the Threat Research Advisory Center at Verizon Business Group, discusses key findings and reviews the security landscape.

Dark Reading
JUNE 2, 2022
The malware targets Windows users via Trojanized downloads of cracked or pirated software and then starts in on cryptocurrency mining and clipboard hijacking.

Data Breach Today
JUNE 2, 2022
Okta's Competitive Win Rates and Renewal Rates Weren't Impacted by the Lapsus$ Hack Okta's competitive win rates and renewal rates weren't measurably impacted by the Lapsus$ cyberattack that came to light in March. The company looked through hundreds opportunities with customers and prospects to see if any of the potential sales were delayed or cancelled due to the breach.

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, VP of Engineering at Betterworks, will explore a practical framework to transform Generative AI pr

Hunton Privacy
JUNE 2, 2022
On May 11, 2022, the French Data Protection Authority (the “CNIL”) published its Annual Activity Report for 2021 (the “Report”). The Report provides an overview of the CNIL’s enforcement activities in 2021. The report notably shows a significant increase in the CNIL’s activity. In particular, the Report revealed that: The CNIL received 14,143 complaints in 2021 (+4% compared to 2020) and closed 12,522.

KnowBe4
JUNE 2, 2022
A smishing campaign is impersonating the UK-based delivery company Evri with text messages informing recipients that their package couldn’t be delivered, according to Paul Ducklin at Naked Security. The messages state that a driver tried to deliver a package, but no one was home. The texts contain a link for the recipient to reschedule their delivery.
eSecurity Planet
JUNE 2, 2022
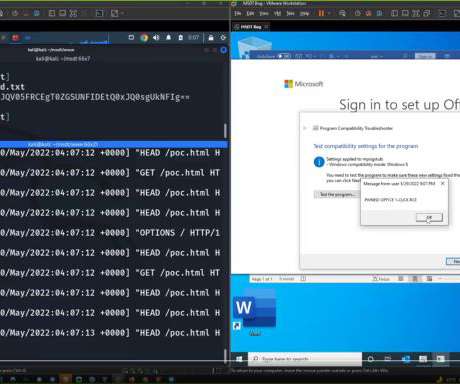
With nearly $200 billion in annual sales, Microsoft is the world’s largest software and information technology (IT) vendor, its products widely used by both companies and consumers. That also makes it the biggest source of vulnerabilities targeted by hackers. According to the U.S. Cybersecurity and Infrastructure Security Agency (CISA), more than a third of all actively exploited vulnerabilities so far this year have been flaws in Microsoft systems.

Schneier on Security
JUNE 2, 2022
Researchers have demonstrated controlling touchscreens at a distance, at least in a laboratory setting: The core idea is to take advantage of the electromagnetic signals to execute basic touch events such as taps and swipes into targeted locations of the touchscreen with the goal of taking over remote control and manipulating the underlying device. The attack, which works from a distance of up to 40mm, hinges on the fact that capacitive touchscreens are sensitive to EMI, leveraging it to inject

Advertisement
Without proper guidance, it’s easy to miss out on Kafka’s full capabilities. While not the easiest technology to optimize, Kafka rewards those willing to explore its depths. Under the hood, it is an elegant system for stream processing, event sourcing, and data integration. Download this white paper to learn the 10 critical rules that will help you optimize your Kafka system and unlock its full potential.

KnowBe4
JUNE 2, 2022
The India-aligned APT SideWinder is using a variety of social engineering techniques to target Pakistani government and military entities, according to researchers at Group-IB. The threat actor is using phishing emails as well as a malicious VPN app placed in the Google Play Store.
Security Affairs
JUNE 2, 2022
The analysis of the internal chats of the Conti ransomware group revealed the gang was working on firmware attack techniques. The analysis of Conti group’s chats , which were leaked earlier this year, revealed that the ransomware gang has been working on firmware attack techniques. An attack against firmware could give threat actors significant powers, they are hard to detect and could be very destructive, and attackers can use them to achieve long-term strategic goals.

Jamf
JUNE 2, 2022
Augmented reality (AR) has enabled new learning models that can be equally effective for students studying on school campuses or isolating at home. Discover how educators at ACS International Schools have successfully integrated AR into K-12 curriculums to enhance learning and empower teachers.
Security Affairs
JUNE 2, 2022
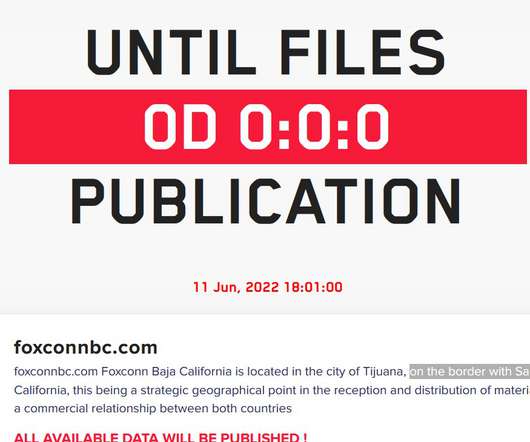
LockBit ransomware gang claimed responsibility for an attack against the electronics manufacturing giant Foxconn that impacted production in Mexico. The electronics manufacturing giant Foxconn confirmed that its production plant in Tijuana (Mexico) has been impacted by a ransomware attack in late May. The LockBit ransomware gang claimed responsibility for an attack and announced that it will release the stolen data by 11 June, 2022 18:01:00 if the company will not pay the ransom.

Advertisement
Generative AI is upending the way product developers & end-users alike are interacting with data. Despite the potential of AI, many are left with questions about the future of product development: How will AI impact my business and contribute to its success? What can product managers and developers expect in the future with the widespread adoption of AI?

Threatpost
JUNE 2, 2022
Melissa Bischoping, security researcher with Tanium and Infosec Insiders columnist, urges firms to consider the upstream and downstream impact of "triple extortion" ransomware attacks.

Dark Reading
JUNE 2, 2022
The threat actor behind the notorious Dridex campaign has switched from using its exclusive credential-harvesting malware to a ransomware-as-a-service model, to make attribution harder.
Security Affairs
JUNE 2, 2022
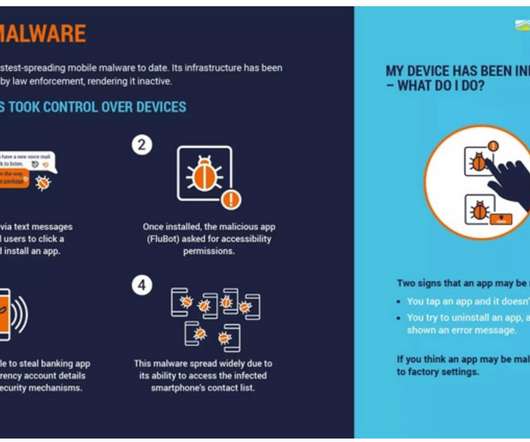
An international law enforcement operation involving 11 countries resulted in the takedown of the FluBot Android malware. An international law enforcement operation involving 11 countries led to the takedown of the infamous FluBot Android malware. The investigation involved law enforcement authorities of Australia, Belgium, Finland, Hungary, Ireland, Spain, Sweden, Switzerland, the Netherlands and the United States, with the coordination of international activity carried out by Europol’s Europea

Dark Reading
JUNE 2, 2022
Although organizations should perform proper risk analysis and patch as soon as practical after there's a fix for this vulnerability, defenders still have options before that's released.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Micro Focus
JUNE 2, 2022
During the month of June, the spotlight is on Pride – and Micro Focus is proud to join the celebration to champion the cause of LGBTQ+ people around the world striving for equality. Being our real selves, and feeling confident and safe in expressing our individuality, are very important to me. I have a deep. View Article. The post Celebrating Pride Month at Micro Focus appeared first on Micro Focus Blog.

Dark Reading
JUNE 2, 2022
Artificial intelligence technology can detect the latest wave of Trickbot ransomware and block the attack before it causes damage.

Threatpost
JUNE 2, 2022
The info-stealing trojan used SMS messages and lifted contact credentials to spread with unprecedented speed across Android devices globally since December 2020.

IG Guru
JUNE 2, 2022
Pilot Testing is Underway with New Version Available on July 15, 2022 [link]. The post ARMA International and the Information Governance Professional Board Announce Updates to the IGP Certification Exam appeared first on IG GURU.

Advertisement
Start-ups & SMBs launching products quickly must bundle dashboards, reports, & self-service analytics into apps. Customers expect rapid value from your product (time-to-value), data security, and access to advanced capabilities. Traditional Business Intelligence (BI) tools can provide valuable data analysis capabilities, but they have a barrier to entry that can stop small and midsize businesses from capitalizing on them.

Thales Cloud Protection & Licensing
JUNE 2, 2022
Protecting the Crown Jewels: The evolution of security strategies and asset protection. divya. Thu, 06/02/2022 - 10:25. Do you know what takes place at the Ceremony of the Keys at the Tower of London? During the 700-year-old ancient ceremony, footsteps echo in the darkness. The sentry cries out, 'Halt, who comes there? 'The Yeoman Warder replies, 'The keys.

Dark Reading
JUNE 2, 2022
Conti threat actors are betting chipset firmware is updated less frequently than other software — and winning big, analysts say.

Rocket Software
JUNE 2, 2022
To meet business goals, organizations worldwide link more processes, exchange more data and share more applications internally with colleagues and externally with global suppliers, partners and clients than any time in the past. . The challenges of moving files, especially product design data (CAD data), database, media, financial and other business-sensitive files in complex and expanding collaboration networks are growing as file sizes also grow.
Let's personalize your content