Experts warn of a spike in APT35 activity and a possible link to Memento ransomware op
Security Affairs
FEBRUARY 2, 2022
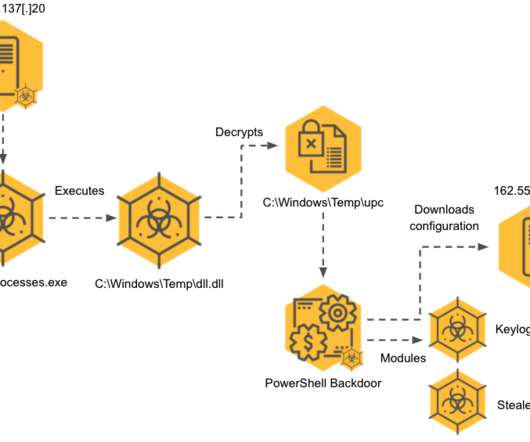
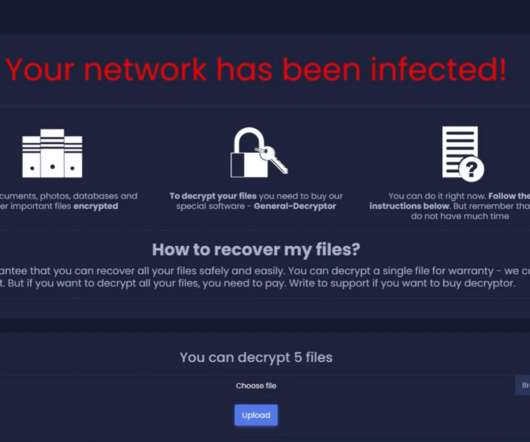
The Cybereason Nocturnus Team reported a spike in the activity of the Iran-linked APT group APT35 (aka Phosphorus or Charming Kitten). The Cybereason Nocturnus Team observed a spike in the activity of the Iran-linked APT group APT35 (aka ‘ Charming Kitten ‘, ‘ Phosphorus ‘, Newscaster , and Ajax Security Team). The Phosphorus group made the headlines in 2014 when experts at iSight issued a report describing the most elaborate net-based spying campaign organized by Iranian hackers using social me





































Let's personalize your content