Sony Investigating Potential Data Breach
Data Breach Today
SEPTEMBER 26, 2023
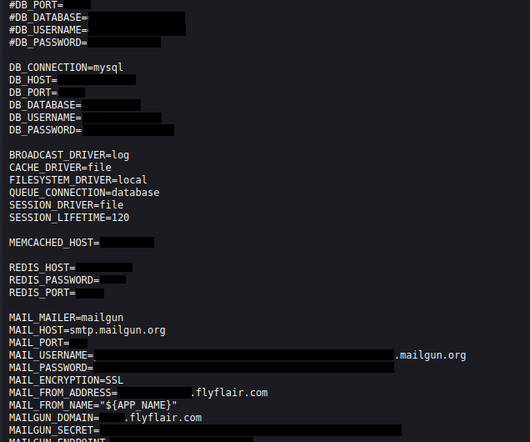
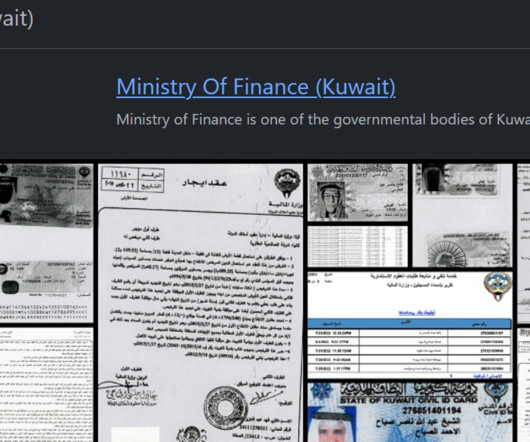
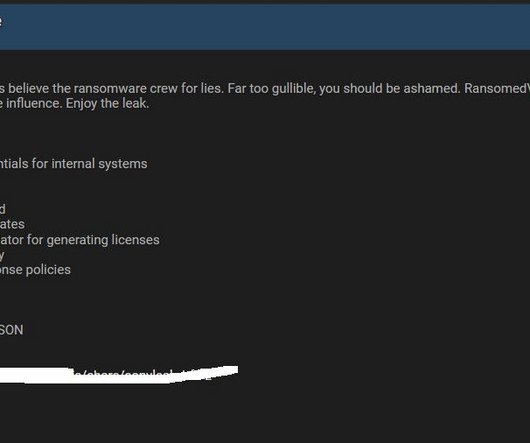
Two Online Threat Actors Claim Responsibility Sony is investigating an apparent leak of internal data posted onto the dark web and a criminal hacking board by separate criminal actors. Sony is saying little other than "we are currently investigating the situation, and we have no further comment at this time.






































Let's personalize your content