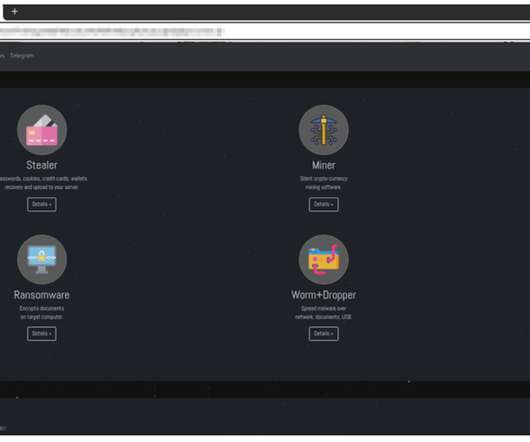
Cybercriminal Faces Prison Time Over Romance Scams and Business Email Compromise Attacks
KnowBe4
OCTOBER 6, 2022
A man from Atlanta, Georgia has been convicted of running romance scams and business email compromise attacks that netted him over $9.5 million, the US Justice Department has announced.









































Let's personalize your content