Recycle Your Phone, Sure, But Maybe Not Your Number
Krebs on Security
MAY 19, 2021
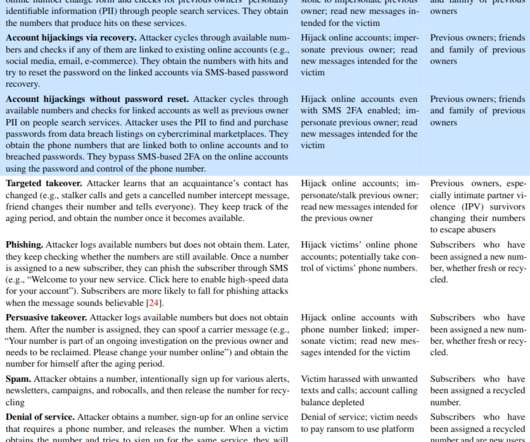
Many online services allow users to reset their passwords by clicking a link sent via SMS, and this unfortunately widespread practice has turned mobile phone numbers into de facto identity documents. Which means losing control over one thanks to a divorce, job termination or financial crisis can be devastating. Even so, plenty of people willingly abandon a mobile number without considering the potential fallout to their digital identities when those digits invariably get reassigned to someone el







































Let's personalize your content