New T-Mobile Breach Affects 37 Million Accounts
Krebs on Security
JANUARY 19, 2023
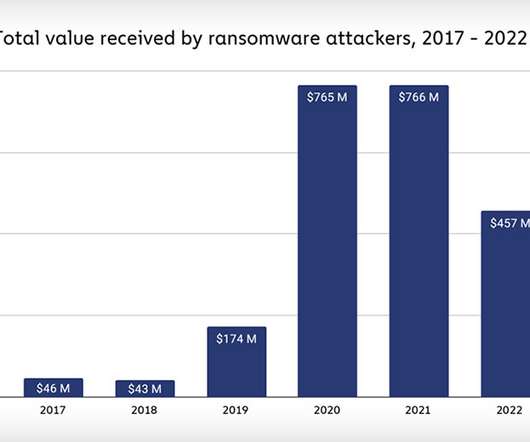
T-Mobile today disclosed a data breach affecting tens of millions of customer accounts, its second major data exposure in as many years. In a filing with federal regulators, T-Mobile said an investigation determined that someone abused its systems to harvest subscriber data tied to approximately 37 million current customer accounts. Image: customink.com In a filing today with the U.S.







































Let's personalize your content