FileTrail Acquires Enterprise Technology Provider Teravine
IG Guru
JANUARY 31, 2022
IG leader will integrate Teravine’s governance solution, enabling FileTrail to provide expanded features and capabilities AUSTIN, Texas — January 18, 2022 — FileTrail®, the leader in modern information governance and records management software for law firms and highly regulated industries, announces its acquisition of Teravine, Inc. Based in Overland Park, Kansas, Teravine has specialized in information governance software as a service […].













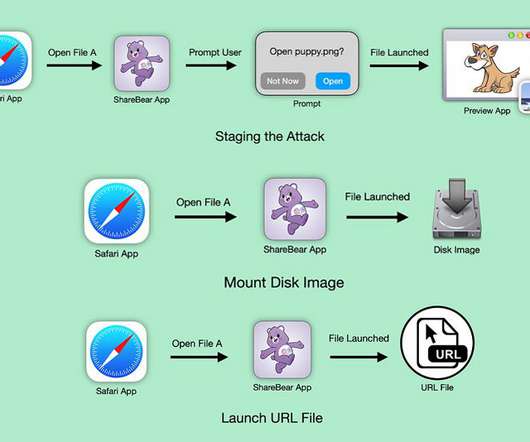





















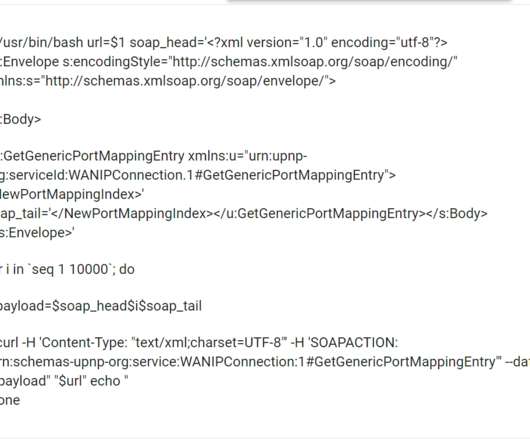







Let's personalize your content