Hackers Are Actively Exploiting Unpatched Adobe ColdFusion
Data Breach Today
MARCH 22, 2023
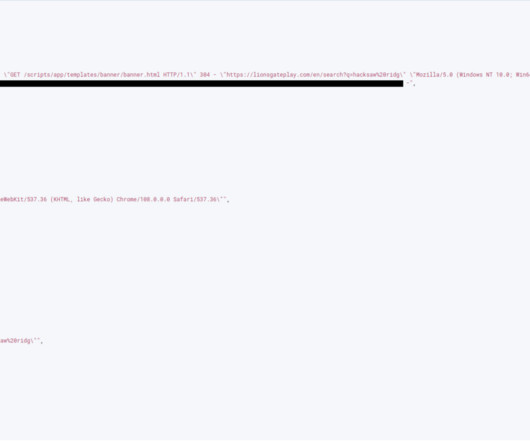
Experts Urge Immediate Patching and Reviewing Servers for Signs of Compromise Hackers have been actively exploiting vulnerabilities in ColdFusion to remotely compromise servers, Adobe warns. Since at least early January, attackers have been dropping web shells via ColdFusion, but it's unclear if only now-known vulnerabilities are being exploited, security researchers say.





































Let's personalize your content