Internet-Exposed Water PLCs Are Easy Targets for Iran
Data Breach Today
FEBRUARY 9, 2024
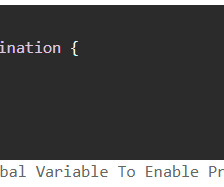
Researchers Find Unprotected Unitronics Devices Here's one reason why Iranian state hackers may have been able to target Israeli-made pressure-monitoring controllers used by American water systems: Nearly 150 of the controllers are exposed to the internet - and some still use the default password 1111.









































Let's personalize your content