Babuk Ransomware Mystery Challenge: Who Leaked Builder?
Data Breach Today
JUNE 29, 2021
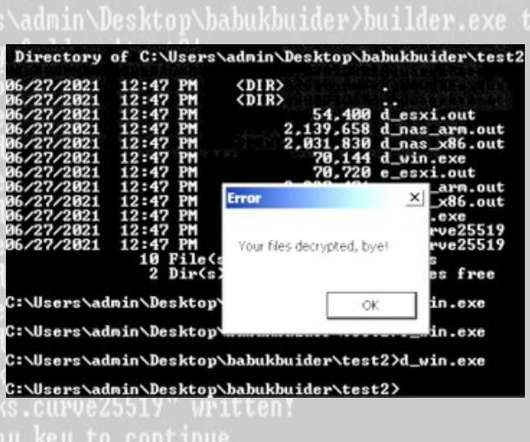
Code for Generating Unique Copies of Crypto-Locking Malware Uploaded to VirusTotal The code used to build copies of Babuk ransomware - to infect victims with the crypto-locking malware - has been leaked, after someone posted the software to virus-scanning service VirusTotal. Whether the leak was intentional - perhaps a rival gang seeking to burn the operation - remains unclear.







































Let's personalize your content