Irish Ransomware Attack Recovery Cost Estimate: $600 Million
Data Breach Today
JUNE 24, 2021
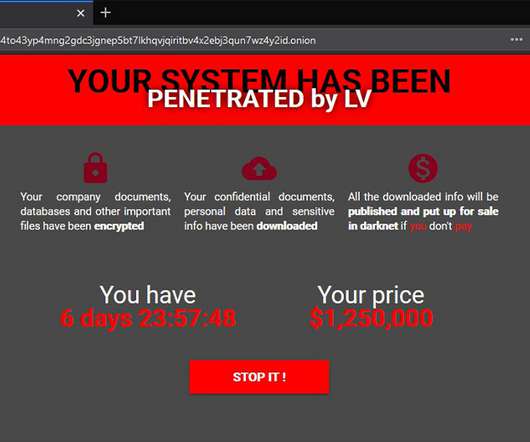
Director of HSE, Nation's Healthcare System, Describes the Costs The recovery costs for the May ransomware attack on Health Service Executive, Ireland's publicly funded healthcare system, is likely to total $600 million, says Paul Reid, HSE's director general.







































Let's personalize your content