Crime Shop Sells Hacked Logins to Other Crime Shops
Krebs on Security
JANUARY 21, 2022
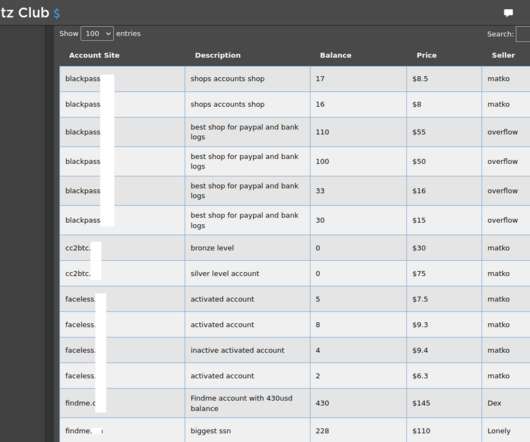
Up for the “Most Meta Cybercrime Offering” award this year is Accountz Club , a new cybercrime store that sells access to purloined accounts at services built for cybercriminals, including shops peddling stolen payment cards and identities, spamming tools, email and phone bombing services, and those selling authentication cookies for a slew of popular websites.
































Let's personalize your content