Arrest in ‘Ransom Your Employer’ Email Scheme
Krebs on Security
NOVEMBER 22, 2021
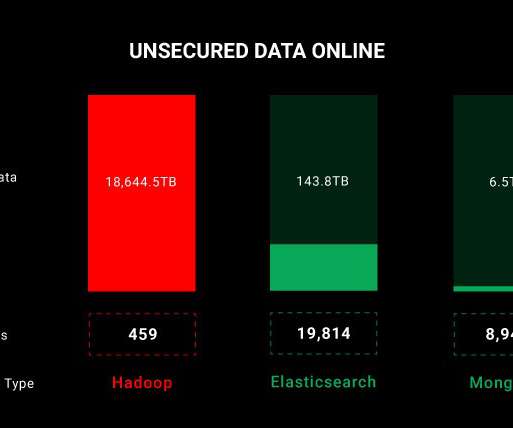
In August, KrebsOnSecurity warned that scammers were contacting people and asking them to unleash ransomware inside their employer’s network, in exchange for a percentage of any ransom amount paid by the victim company. Image: Abnormal Security. On the contrary: This activity pumps a great deal of Western money into Nigeria.


















Let's personalize your content