Italy announced its National Cybersecurity Strategy 2022/26
Security Affairs
MAY 26, 2022
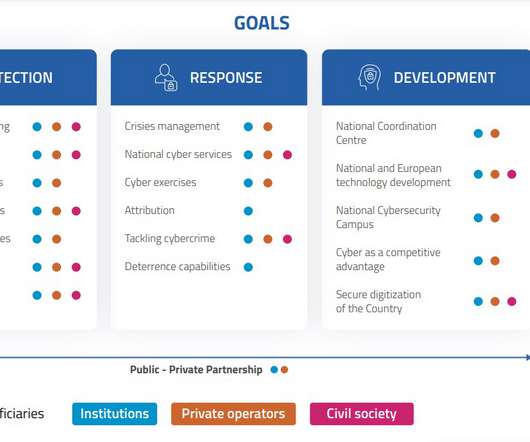
Italy announced its National Cybersecurity Strategy for 2022/26, a crucial document to address cyber threats and increase the resilience of the country. The threat landscape rapidly changes and urges the government to review its strategy and propose a series of objectives to achieve in the next four years.




















Let's personalize your content