Data collection cheat sheet: how Parler, Twitter, Facebook, MeWe’s data policies compare
Security Affairs
JANUARY 13, 2021
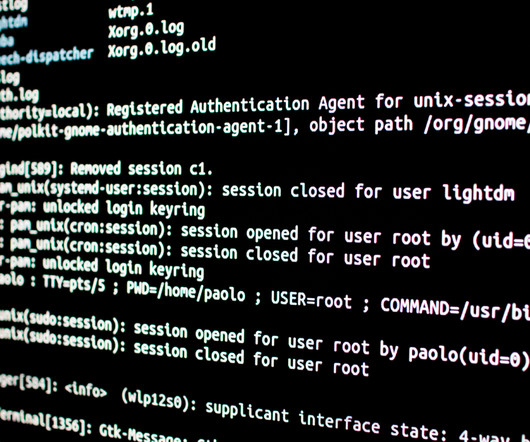
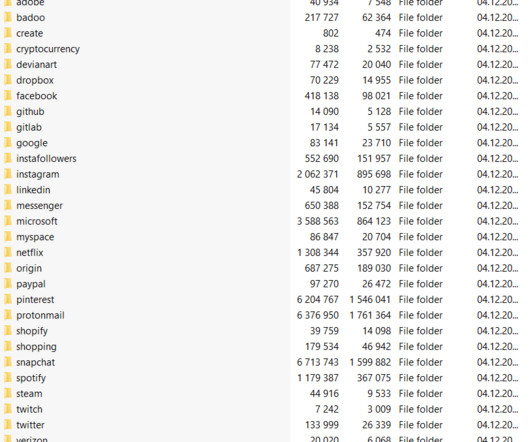
To make matters even worse for the platform, a security researcher was able to collect more than 70 terabytes, which equals 70,000 gigabytes, of Parler users’ messages, videos, audio, and all other activity. How this data was collected and processed.
















Let's personalize your content