Researchers show how to steal a Tesla Model X in a few minutes
Security Affairs
NOVEMBER 23, 2020
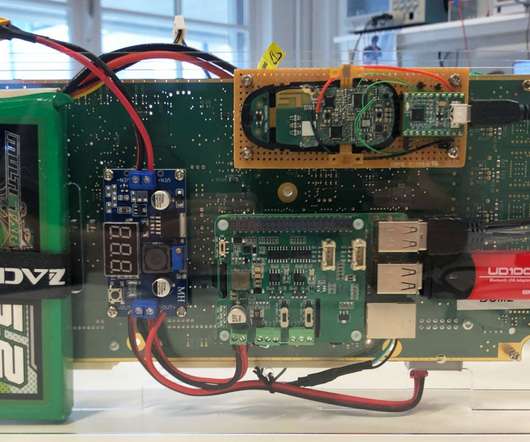
Boffins have demonstrated how to steal a Tesla Model X in a few minutes by exploiting vulnerabilities in the car’s keyless entry system. The experts discovered that the updating mechanism for the software running on the Bluetooth chip of the key fob is not secure. Pierluigi Paganini. SecurityAffairs – hacking, Tesla Model X).





































Let's personalize your content