Experts linked Maui ransomware to North Korean Andariel APT
Security Affairs
AUGUST 9, 2022
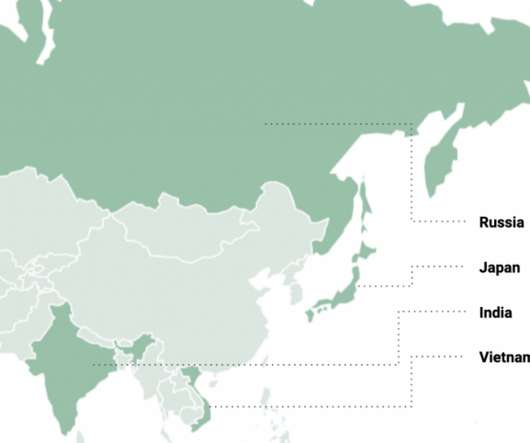
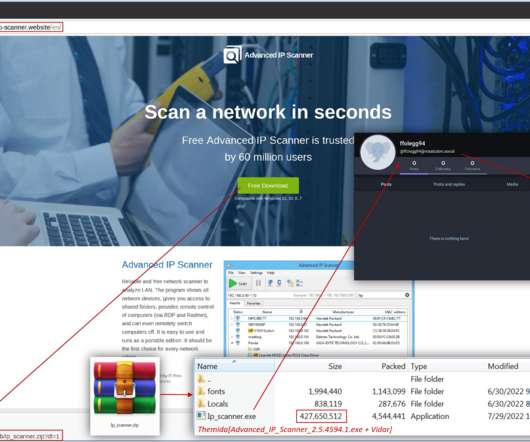
Cybersecurity researchers from Kaspersky linked the Maui ransomware to the North Korea-backed Andariel APT group. Kaspersky linked with medium confidence the Maui ransomware operation to the North Korea-backed APT group Andariel , which is considered a division of the Lazarus APT Group, . At the time, the U.S.




























Let's personalize your content