Iranian Group Likely Behind Albanian Government Attack
Data Breach Today
AUGUST 4, 2022
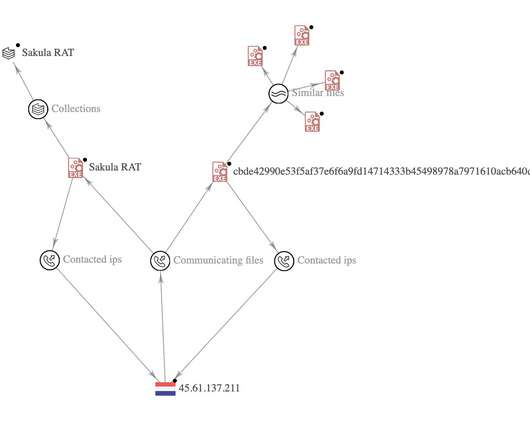
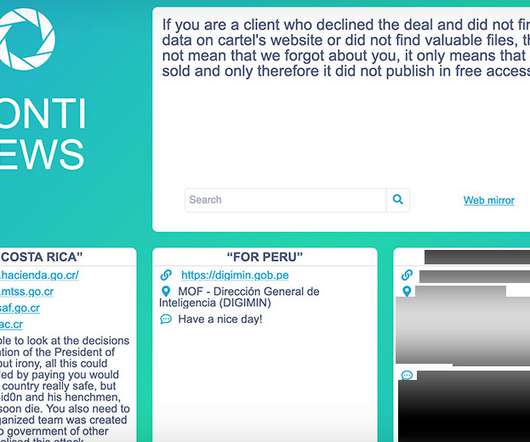
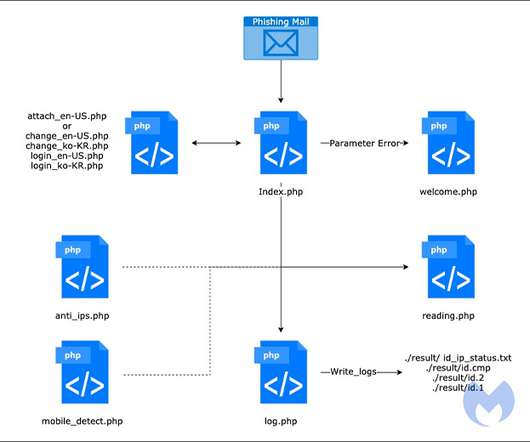
Group Published Ransomware Execution Video on Website A cyberattack that temporarily paralyzed Albania's pivot to digital government likely came from Iranian hackers.









































Let's personalize your content