Updated Kmsdx botnet targets IoT devices
Security Affairs
AUGUST 28, 2023
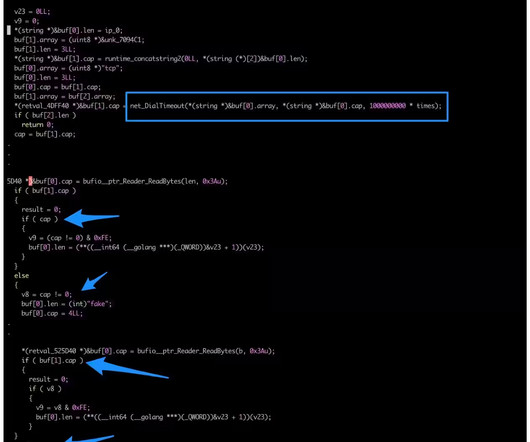
The Akamai Security Intelligence Response Team (SIRT) discovered a new version of the KmsdBot botnet that employed an updated Kmsdx binary targeting Internet of Things (IoT) devices. The malware was employed in cryptocurrency mining campaigns and to launch denial-of-service (DDoS) attacks.


























Let's personalize your content