Weakness at the Network Edge: Mandiant Examines 2022’s Zero-Day Exploits
eSecurity Planet
MARCH 27, 2023
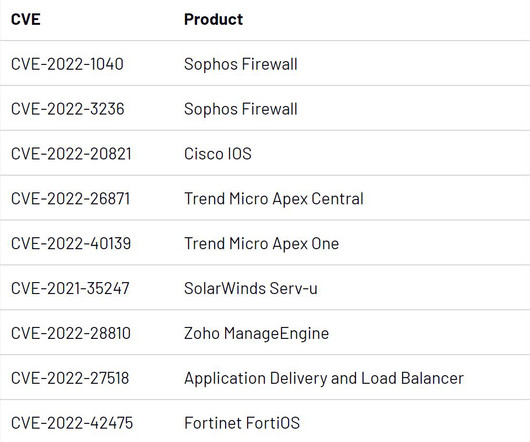
Follina , is a vulnerability in Microsoft Diagnostics Tool (MDST), exploited by persuading victims to open Word documents, which can enable the attacker to execute arbitrary code. In the meantime, Mandiant urges organizations to prioritize patching in order to mitigate risk.

















Let's personalize your content