TinyNuke banking malware targets French organizations
Security Affairs
DECEMBER 13, 2021
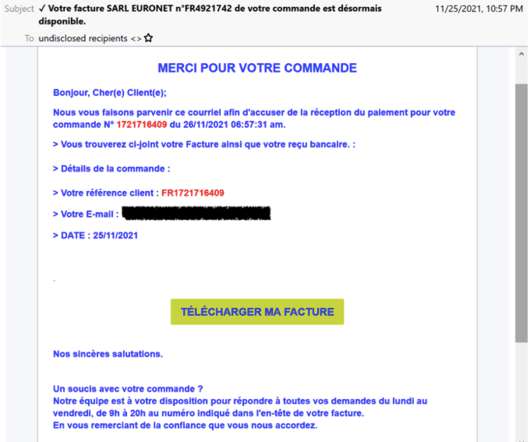
The TinyNuke malware is back and now was used in attacks aimed at French users working in manufacturing, technology, construction, and business services. “In the most recent campaigns, the threat actor uses invoice-themed lures purporting to be logistics, transportation, or business services entities.”



























Let's personalize your content