ViperSoftX uses more sophisticated encryption and anti-analysis techniques
Security Affairs
APRIL 29, 2023
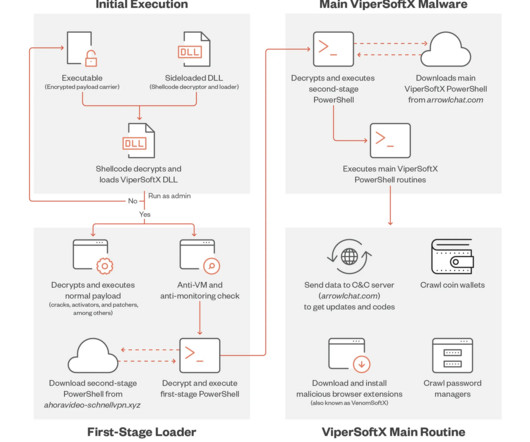
Trend Micro researchers observed a new ViperSoftX malware campaign that unlike previous attacks relies on DLL sideloading for its arrival and execution technique. ” reads the analysis published by Trend Micro. ” reads the analysis published by Trend Micro. ViperSoftX is back, doesn't look like much has changed.
















































Let's personalize your content