GUEST ESSAY: In pursuit of smarter cybersecurity — to overcome complex risks and grow revenue
The Last Watchdog
JANUARY 8, 2023
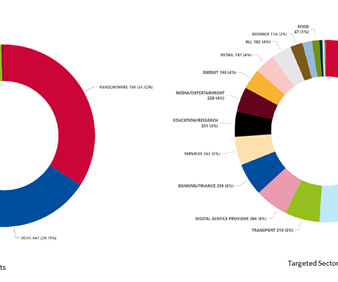
A security strategy should clear obstacles and enable every part of a business operation to run smoothly. Departments such as support, manufacturing, design, services, and delivery are enhanced by smart security measures, which allay distracting setbacks and increase the overall inertia. What constitutes “smarter security?”




































Let's personalize your content