How Jamworks protects confidentiality while integrating AI advantages
IBM Big Data Hub
JANUARY 12, 2024
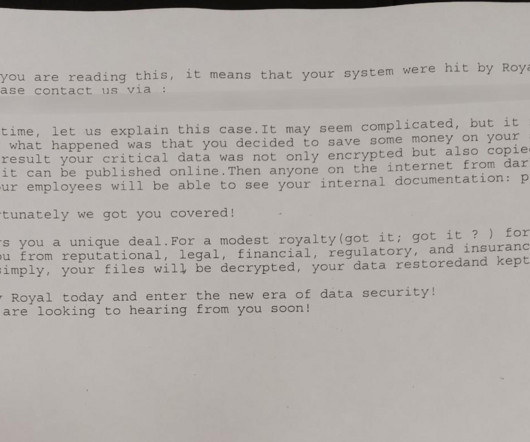
“AI is driving a revolution in education, accessibility and productivity. Robust encryption, granular access controls and privacy-preserving techniques become imperative to counter the risks of unauthorized data access and use. Jamworks has two core products: Jamworks for Education and Jamworks for Business.



































Let's personalize your content