A Microsoft 365 feature can ransom files on SharePoint and OneDriveCould
Security Affairs
JUNE 17, 2022
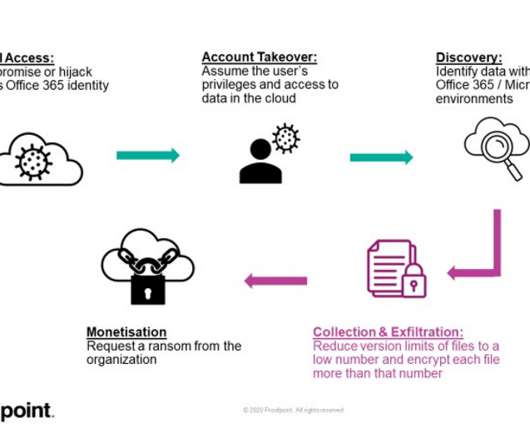
Experts discovered a feature in Microsoft 365 suite that could be abused to encrypt files stored on SharePoint and OneDrive and target cloud infrastructure. Researchers from Proofpoint reported that a feature in the in Microsoft 365 suite could be abused to encrypt files stored on SharePoint and OneDrive. ” continues the report.


























Let's personalize your content