Attackers use encrypted RPMSG messages in Microsoft 365 targeted phishing attacks
Security Affairs
MAY 29, 2023
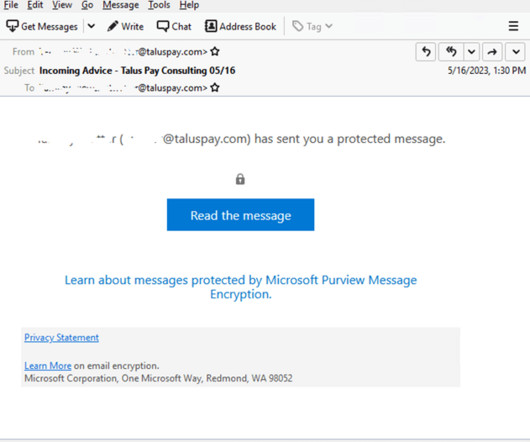
Experts warn of phishing attacks that are combining the use of compromised Microsoft 365 accounts and.rpmsg encrypted emails. Trustwave researchers have observed threat actors using encrypted RPMSG attachments sent via compromised Microsoft 365 accounts in a phishing campaign aimed at stealing Microsoft credentials.











































Let's personalize your content