US CISA Aims to Expand Automated Malware Analysis Support
Data Breach Today
APRIL 10, 2024
US Cyber Defense Agency Scales Next-Generation Malware Analysis Platform The U.S.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 automated-malware-analysis
automated-malware-analysis 
Data Breach Today
APRIL 10, 2024
US Cyber Defense Agency Scales Next-Generation Malware Analysis Platform The U.S.
Security Affairs
APRIL 21, 2024
The experts detected only two CR4T implants, but they speculate the existence of many other variants which may be completely different malware. The threat actors behind the DuneQuixote campaign took steps to prevent collection and analysis the implants through the implementation of practical and well-designed evasion methods.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
JANUARY 17, 2024
The analysis revealed that the infections left traces in the Shutdown.log, which is a text-based log file. ” reads the analysis published by Kaspersky. The analysis of the infections also revealed other similarities such as the path associated with malware execution (“/private/var/db/”). ” concludes Kaspersky.

The Last Watchdog
NOVEMBER 14, 2023
Obama’s clarion call led to the passage of the Cybersecurity Information Sharing Act , the creation of Information Sharing and Analysis Organizations ( ISAOs ) and the jump-starting of several private-sector sharing consortiums. From this command center perspective, real-world strategic analysis happens continuously and in real time.
Security Affairs
AUGUST 28, 2023
.” Below is a watch video that shows this attack technique: The JPCERT experts say that the OLEVBA analysis tool for malicious Word files can be used to detect malicious files crafted to carry out this attack technique However, popular PDF analysis tools like ‘pdfid’ may be not able to detect the malicious file.

Security Affairs
FEBRUARY 1, 2024
Mandiant spotted new malware used by a China-linked threat actor UNC5221 targeting Ivanti Connect Secure VPN and Policy Secure devices. Mandiant researchers discovered new malware employed by a China-linked APT group known as UNC5221 and other threat groups targeting Ivanti Connect Secure VPN and Policy Secure devices.

Lenny Zeltser
JANUARY 6, 2021
Malware analysis sits at the intersection of incident response, forensics, system and network administration, security monitoring, and software engineering. As someone who’s helped thousands of security professionals learn how to analyze malware at SANS Institute , I have a few tips for how you can get started.
Security Affairs
SEPTEMBER 26, 2023
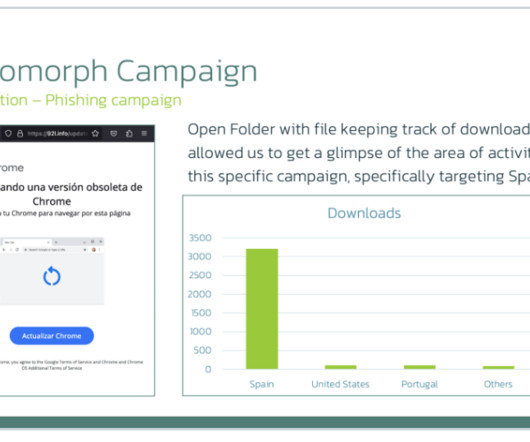
A new campaign is spreading Xenomorph malware to Android users in the United States, Spain, Portugal, Italy, Canada, and Belgium. Researchers from ThreatFabric uncovered a new campaign spreading Xenomorph malware to Android users in the United States and all over the world. that was significantly improved.

Security Affairs
JULY 15, 2022
Dragos researchers uncovered a small-scale campaign targeting industrial engineers and operators with Sality malware. During a routine vulnerability assessment, Dragos researchers discovered a campaign targeting industrial engineers and operators with Sality malware. “Dragos only tested the DirectLogic-targeting malware.

Dark Reading
MARCH 14, 2018
Researchers at Black Hat Asia will demonstrate a new framework they created for catching and studying Apple MacOS malware.
Security Affairs
MARCH 10, 2023
A new version of the Xenomorph Android malware includes a new automated transfer system framework and targets 400 banks. The author of the Xenomorph Android malware, the Hadoken Security Group, continues to improve their malicious code. Experts warn that a new variant recently discovered, tracked as Xenomorph.C,

Security Affairs
JANUARY 21, 2024
Patch it now! million cryptojacking scheme arrested in Ukraine Cybercrime Cryptojacker arrested in Ukraine over EUR 1.8 million cryptojacking scheme arrested in Ukraine Cybercrime Cryptojacker arrested in Ukraine over EUR 1.8
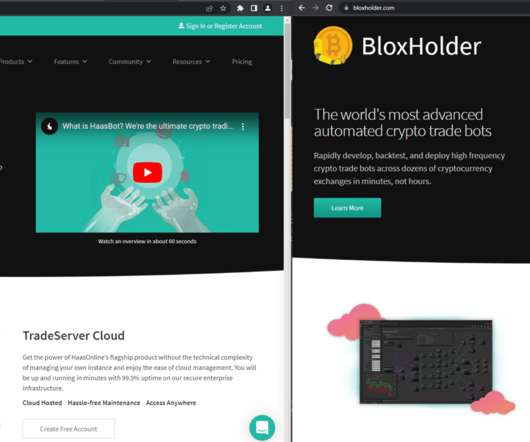
Security Affairs
DECEMBER 4, 2022
The North Korea-linked Lazarus APT spreads fake cryptocurrency apps under the fake brand BloxHolder to install the AppleJeus malware. Volexity researchers warn of a new malware campaign conducted by the North Korea-linked Lazarus APT against cryptocurrency users. “continues the analysis.
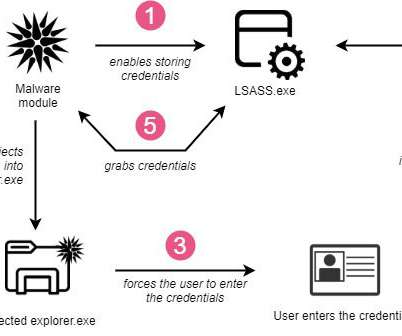
Security Affairs
FEBRUARY 16, 2022
TrickBot malware is targeting customers of 60 financial and technology companies with new anti-analysis features. The infamous TrickBot malware was employed in attacks against customers of 60 financial and technology companies with new anti-analysis features. ” reads the analysis published by CheckPoint.
Security Affairs
FEBRUARY 14, 2023
Threat actors published more than 451 unique malware-laced Python packages on the official Python Package Index (PyPI) repository. Phylum researchers spotted more than 451 unique Python packages on the official Python Package Index (PyPI) repository in an attempt to deliver clipper malware on the developer systems.
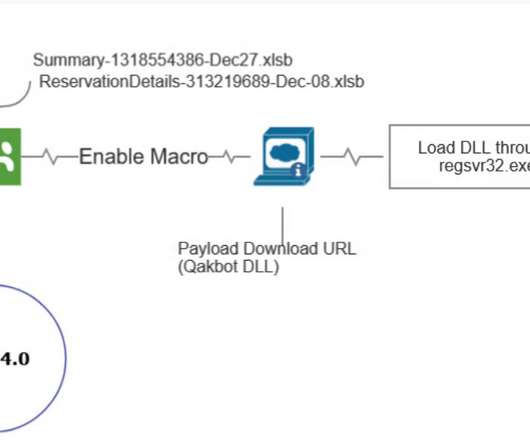
Security Affairs
JULY 13, 2022
Experts warn that operators behind the Qakbot malware operation are improving their attack chain in an attempt to avoid detection. Qakbot , also known as QBot, QuackBot and Pinkslipbot, is an info-stealing malware that has been active since 2008. The malware spreads via malspam campaigns, it inserts replies in active email threads.
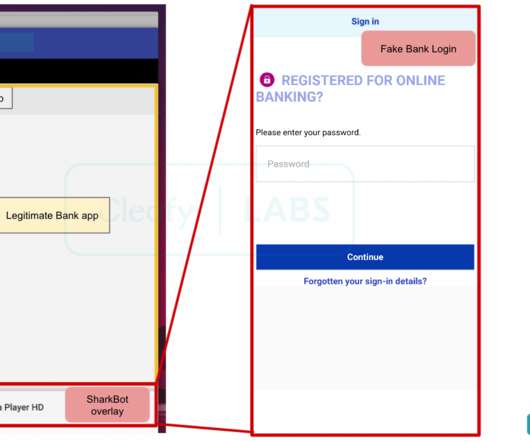
Security Affairs
NOVEMBER 15, 2021
The malware has been active at least since late October 2021, it targeting the mobile users of banks in Italy, the UK, and the US. The malware implements multiple anti-analysis techniques, including string obfuscation routine, emulator detection and a domain generation algorithm (DGA). ” concludes the report.
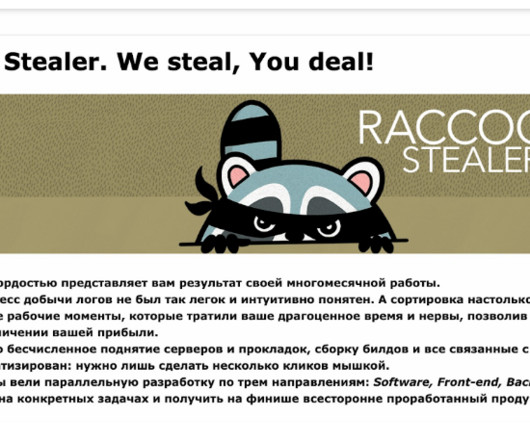
Security Affairs
FEBRUARY 19, 2024
Raccoon is offered for sale as a malware-as-a-service (MaaS) that implements an easy-to-use automated backend panel, operators also offer bulletproof hosting and 24/7 customer support in both Russian and English. The malware is now promoted on English-speaking hacking forums, it works on both 32-bit and 64-bit operating systems.

Security Affairs
JANUARY 6, 2023
The experts state that malware creators abuse legitimate functionalities and implement various techniques to exploit vulnerabilities, evade defenses, or trick users into infecting their devices. “The ransomware families we analyzed often share similar anti-analysis and persistence techniques. ” Microsoft concludes.

Security Affairs
MAY 26, 2021
Kubernetes is an open-source container-orchestration system for automating computer application deployment, scaling, and management. The TeamTNT botnet is a crypto-mining malware operation that has been active since April 2020 and that targets Docker installs. The malware deploys the XMRig mining tool to mine Monero cryptocurrency.
Security Affairs
APRIL 19, 2022
Researchers disclosed a new variant of the SolarMarker malware that implements new techniques to avoid detection. Cybersecurity researchers from Palo Alto Networks disclosed a new version of the SolarMarker malware that implements new features to avoid detection. ” reads the analysis published by PaloAlto Networks.
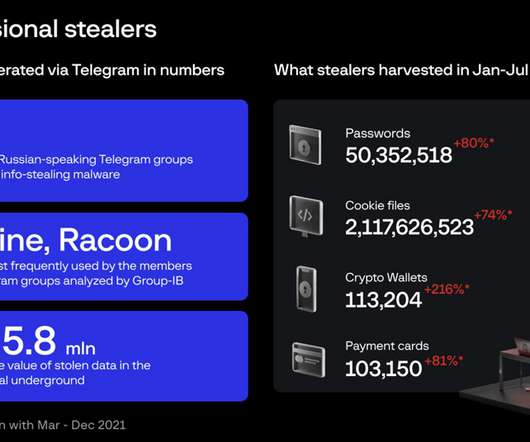
eSecurity Planet
NOVEMBER 29, 2022
Group-IB cybersecurity researchers recently identified several Russian-speaking cybercrime groups offering infostealing malware-as-a-service (MaaS), resulting in the theft of more than 50 million passwords thus far. Eight of the groups use Raccoon malware, 23 use Redline, and three use custom stealers. Aurora Malware.

Lenny Zeltser
JULY 22, 2020
This Linux distribution for malware analysis includes hundreds of new and classic tools for examining executables, documents, scripts, and other forms of malicious code. To achieve this, the distro now uses SaltStack behind the scenes for automating the installation and configuration of software.

Lenny Zeltser
SEPTEMBER 26, 2019
What malware analysis approaches work well? The following discussion–captured as an MP3 audio file –offers friendly advice from 5 malware analysts. 1:05) How has your approach to examining malware changed over the years? (7:17) 7:17) What role do automated sandboxes play in the analysis process? (14:30)

The Last Watchdog
MAY 11, 2021
The payload malware: Sunburst, a heavily-obfuscated backdoor. People tend to focus on the Sunburst malware , the actual backdoor that ended up in the affected update package,” Pericin told me. Out of this comes whitelists and blacklists on which malware filters are based. Granular scrutiny.
Security Affairs
JUNE 1, 2022
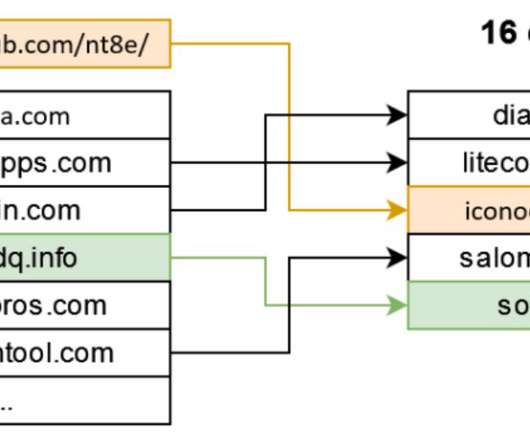
XLoader has been observed since 2020, it is a very cheap malware strain that is based on the popular Formbook Windows malware. . XLoader and Formbook shares the same structure of configuration, the 64 domains from the malware configuration are actually decoys, used as a diverse strategy. SecurityAffairs – hacking, malware).

The Last Watchdog
MARCH 24, 2020
Related: ‘ Risk-based’ analysis used in SOAR At RSA 2020 , I learned about yet another emerging approach, with supporting technology, called Security Operations Platform (SOP.) Unified workspace Young describes QuoLab’s flagship product as a “data fusion, investigation and analysis platform with a collaborative spin.”
Security Affairs
JUNE 13, 2023
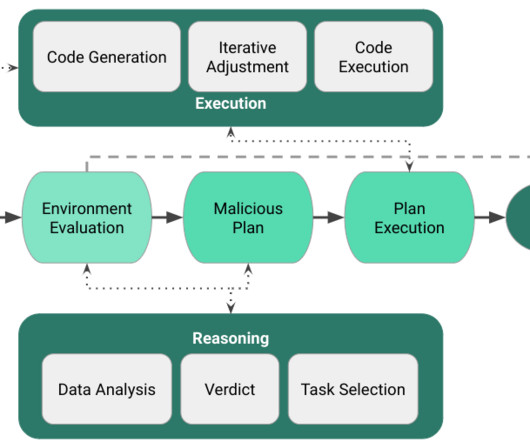
Malware researchers analyzed the application of Large Language Models (LLM) to malware automation investigating future abuse in autonomous threats. We adopted an iterative code generation approach to leverage LLMs in the complicated task of generating code on the fly to achieve the malicious objectives of the malware agent.
eSecurity Planet
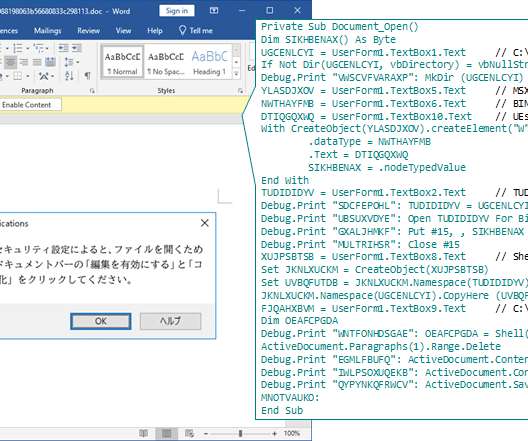
NOVEMBER 7, 2022
Kaspersky researchers recently found evidence of an advanced threat group continuously updating its malware to evade security products, similar to a release cycle for developers. The sophisticated malware was hidden in malicious Word file attachments. However, the same also goes for antivirus software and other anti-malware solutions.

Security Affairs
DECEMBER 23, 2021
Sophos experts monitoring AvosLocker ransomware attacks, noticed that the malware is rebooting compromised systems into Windows Safe Mode to disable endpoint security solutions. ” reads the analysis published by Sophos. ” continues the analysis. ” concludes the report. Pierluigi Paganini.

Security Affairs
DECEMBER 17, 2023
Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press. CISA and ENISA enhance their Cooperation CISA adds Qlik bugs to exploited vulnerabilities catalog Report: 2.6 CISA and ENISA enhance their Cooperation CISA adds Qlik bugs to exploited vulnerabilities catalog Report: 2.6
Security Affairs
JULY 25, 2022
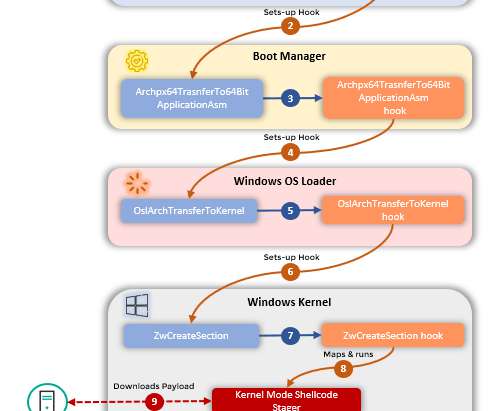
This malware was first spotted by Chinese firm Qihoo360 in 2017. The researchers were not able to determine the initial attack vector, but the analysis of the malicious code allowed the experts to discover which devices can be infected by the CosmicStrand. ” reads the analysis published by the experts.
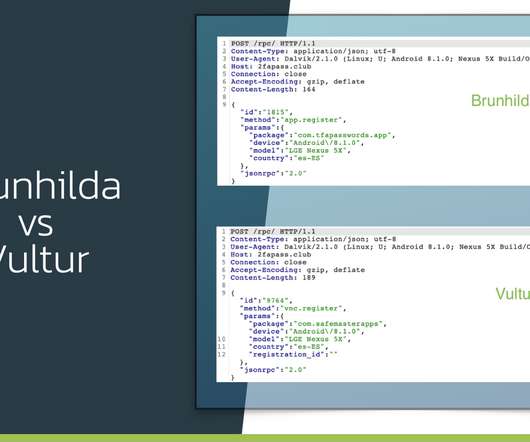
Security Affairs
JULY 31, 2021
“For the first time we are seeing an Android banking trojan that has screen recording and keylogging as main strategy to harvest login credentials in an automated and scalable way. ” reads the analysis published by ThreatFabric. Experts believe that the malware has already infected thousands of devices.

Krebs on Security
NOVEMBER 17, 2020
In many cases, the notification approval requests themselves are deceptive — disguised as prompts to click “OK” to view video material, or as “CAPTCHA” requests designed to distinguish automated bot traffic from real visitors. One notification was an ad for Norton antivirus; the other was for McAfee.

Security Affairs
JUNE 4, 2023
Xplain hack impacted the Swiss cantonal police and Fedpol Zyxel published guidance for protecting devices from ongoing attacks Kimsuky APT poses as journalists and broadcast writers in its attacks New Linux Ransomware BlackSuit is similar to Royal ransomware CISA adds Progress MOVEit Transfer zero-day to its Known Exploited Vulnerabilities catalog (..)

eSecurity Planet
DECEMBER 19, 2023
Automated Security Updates & Patching The underlying hardware and software infrastructure is managed and maintained by IaaS providers. Automated updates guarantee that vulnerabilities are fixed as soon as possible, lowering the risk of exploitation. This involves managing operating system and component security updates and fixes.

eSecurity Planet
SEPTEMBER 1, 2023
IDPS recognizes and blocks common threats such as specific malware or intrusion attempts by utilizing a database of known attack patterns (signatures). Behavioral Analysis Behavioral analysis , a machine learning-driven approach, assesses cloud workload and app activity to identify possible security issues.

Security Affairs
NOVEMBER 18, 2021
The attackers initially conducted a reconnaissance phase by probing the e-store with automated eCommerce attack probes. The analysis of the backdoor revealed that it was able to receive commands from a server hosted on Alibaba (47.113.202.35). . “At the time of writing, no other anti-virus vendor recognize this malware.

eSecurity Planet
APRIL 1, 2024
Vendors and researchers disclosed a wide range of vulnerabilities this week from common Cisco IOS, Fortinet, and Windows Server issues to more focused flaws affecting developers (PyPI), artificial intelligence (Ray, NVIDIA), and industrial controls (Rockwell Automation).

eSecurity Planet
APRIL 23, 2021
To fill this gap and aid in the analysis, detection, and testing of malware, sandboxing is widely used to give organizations the setting, isolation, and security tools needed to preserve the integrity of the host network. Sandbox solutions today are compared today by their set of features to aid advanced malware analysis.

The Last Watchdog
MARCH 23, 2020
Related: ‘ Risk-based’ analysis used in SOAR At RSA 2020 , I learned about yet another emerging approach, with supporting technology, called Security Operations Platform (SOP.) Unified workspace Young describes QuoLab’s flagship product as a “data fusion, investigation and analysis platform with a collaborative spin.”

eSecurity Planet
JULY 16, 2021
Incident response tools can help implement incident response plans and elevate response plans from a manual to an automated basis, sandboxing threats and shutting down ports and access and the like. Ransomware, virus, and malware removal. The whole idea is to have a systematic approach to incidents rather than acting haphazardly.
Security Affairs
MARCH 27, 2023
Supply chain security firm Phylum discovered a malicious Python package on the Python Package Index (PyPI) repository that uses Unicode to evade detection and deliver information-stealing malware. The analysis of the package revealed that it supports data harvesting capabilities. ” reads the analysis published by Phylum.”However,
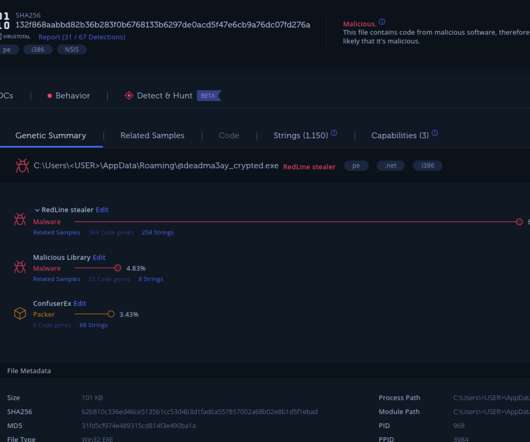
Security Affairs
JUNE 29, 2022
Researchers detailed a new information-stealing malware, dubbed YTStealer, that targets YouTube content creators. Intezer cybersecurity researchers have detailed a new information-stealing malware, dubbed YTStealer, that was developed to steal authentication cookies from YouTube content creators. ” continues the report.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content