Possible Chinese Hackers Exploit Microsoft Exchange 0-Days
Data Breach Today
OCTOBER 1, 2022
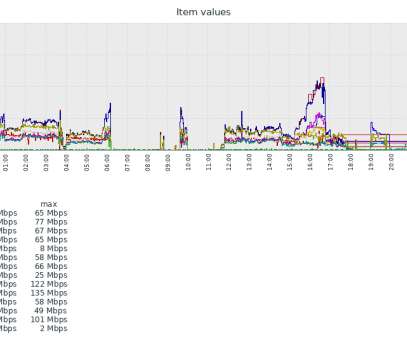
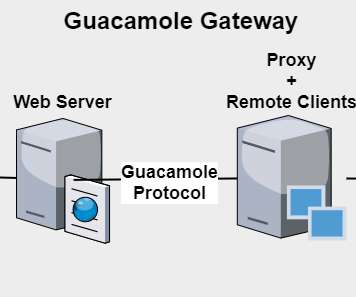
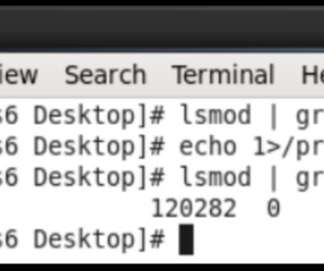
No Patch Yet Available Although Exploitation Requires Authenticated Access Hackers, possibly Chinese, are exploiting Microsoft Exchange zero-day vulnerabilities to apparently implant backdoors and steal credentials. The computing giant says it doesn't yet have a patch, telling systems administrators to instead implement workarounds.











































Let's personalize your content