Experian’s Credit Freeze Security is Still a Joke
Krebs on Security
APRIL 26, 2021
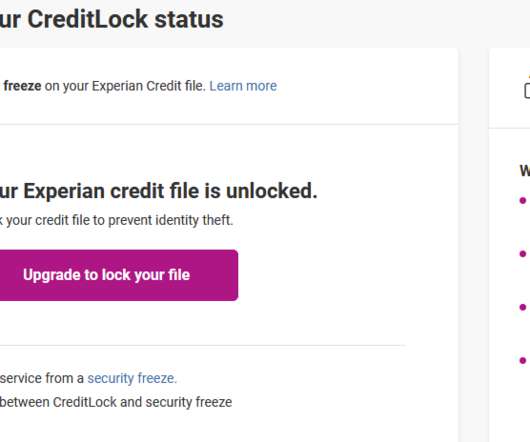
Last week, KrebsOnSecurity heard from a reader who had his freeze thawed without authorization through Experian’s website, and it reminded me of how truly broken authentication and security remains in the credit bureau space. “They’re allowing this huge security gap so they can make a profit. and $24.99

































Let's personalize your content