UK ICO Reprimands London Hackney Council for 2020 Hack
Data Breach Today
JULY 17, 2024
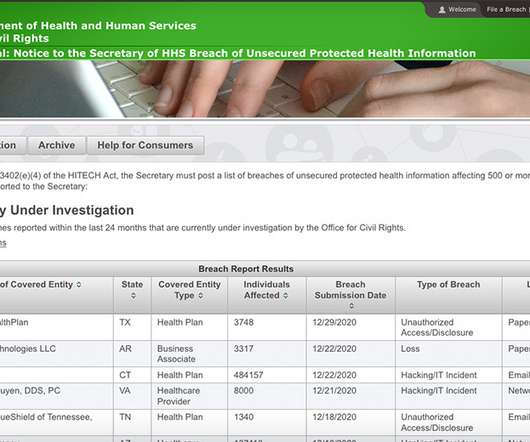
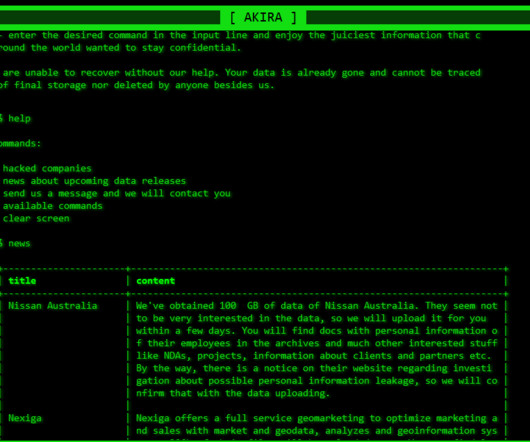
The Pysa ransomware group claimed credit for encrypting 440,000 files in 2020. s data watchdog on Wednesday reprimanded London's Hackney Council over its failure to protect the data of nearly 280,000 town residents from a ransomware hack that resulted in attackers leaking sensitive data.


















































Let's personalize your content