Norton 360 Now Comes With a Cryptominer
Krebs on Security
JANUARY 6, 2022
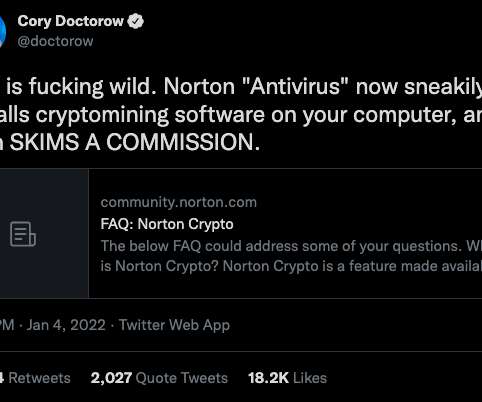
Norton 360 , one of the most popular antivirus products on the market today, has installed a cryptocurrency mining program on its customers’ computers. In 2017, the identity theft protection company LifeLock was acquired by Symantec Corp. In 2017, the identity theft protection company LifeLock was acquired by Symantec Corp.






















Let's personalize your content